This post will show the process for capturing packets from a login to an unsecured website and subsequently analyzing those packets to find the login credentials in clear text.
For this exercise, a VPN was established with the tryhackme room, Lazy Admin, through OpenVPN on a Kali Linux VM.
To begin, open a terminal in Kali Linux and use tcpdump to set up a packet capture for the appropriate interface. In this case, the interface tun0 was used.
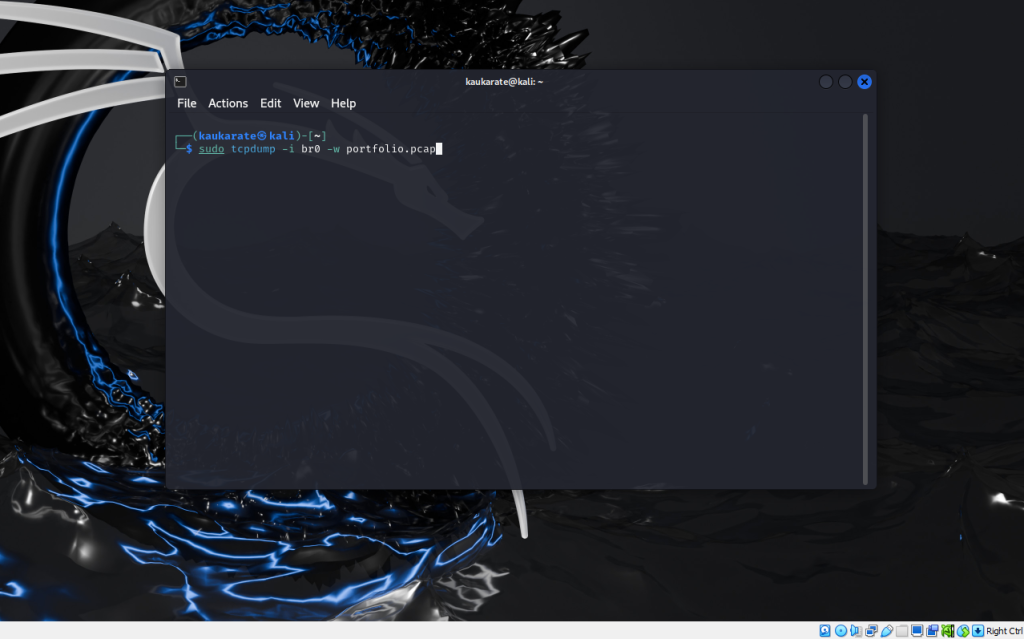
The command above requires sudo permission to run the packet capture. The ‘-i’ portion denotes which interface to capture packets from and the ‘-w’ portion creates a file to which the captured packets will be written.
Next, run the command and move over to a web browser to perform the unsecured login to be captured.
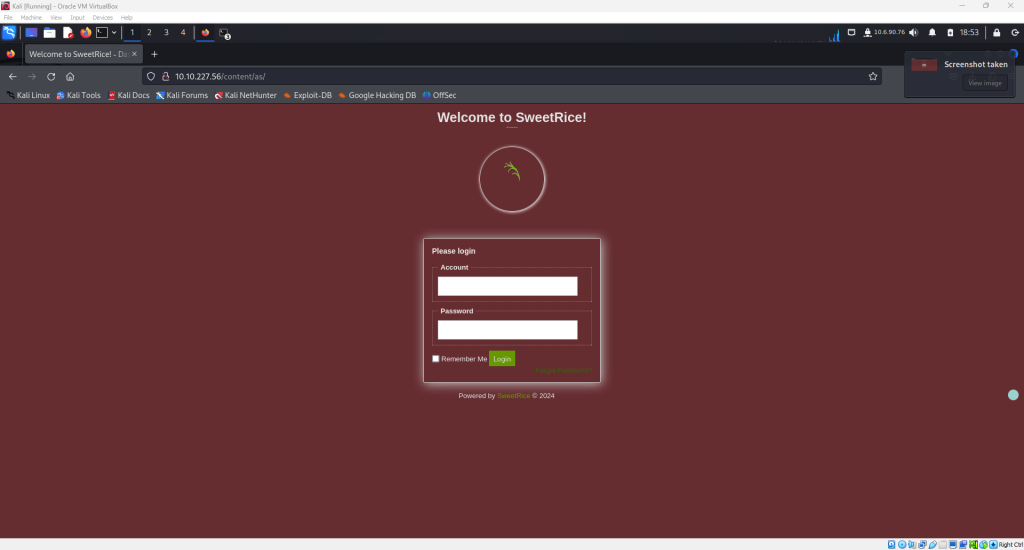
In a previous post, the URL and login credentials were determined for this SweetRice CMS site. Enter those credentials here and the following page will be displayed.
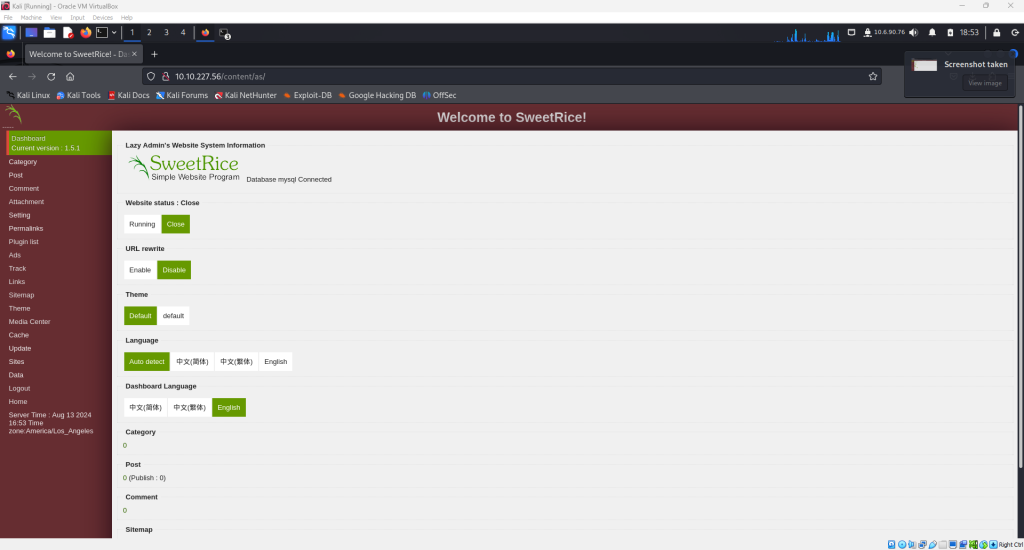
Now, return to the terminal running tcpdump and use Ctrl+C to end the capture process.
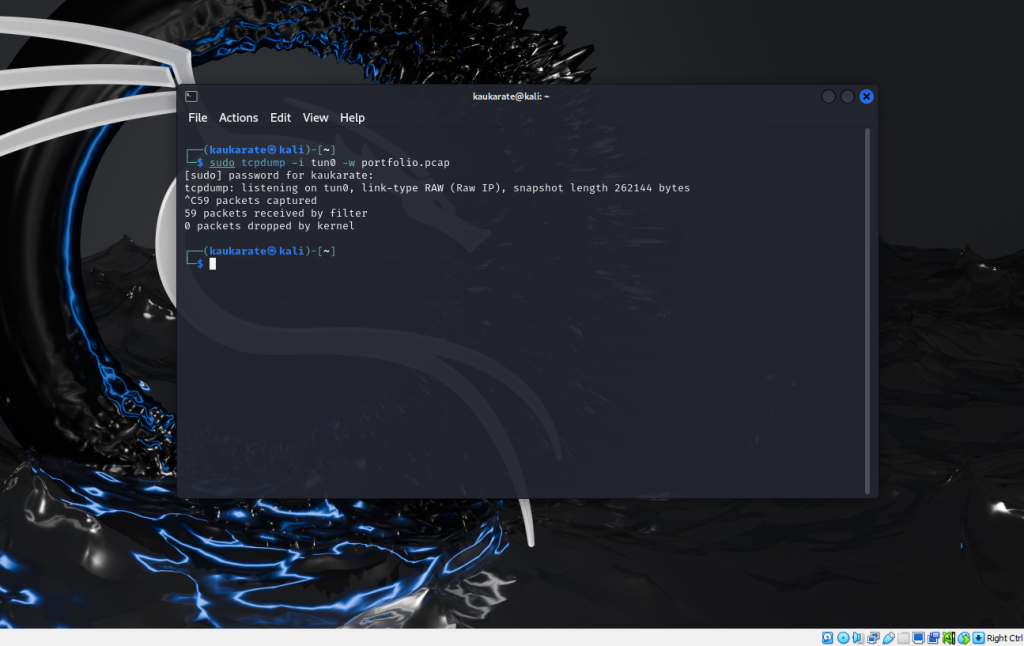
At this step, a file containing the captured packets has been created and can be analyzed. Open Wireshark to perform the analysis.
Select “Open” under “File” in the top left corner and choose the file created in the previous step.
The contents of the packet capture file will be displayed and look something like the image below.
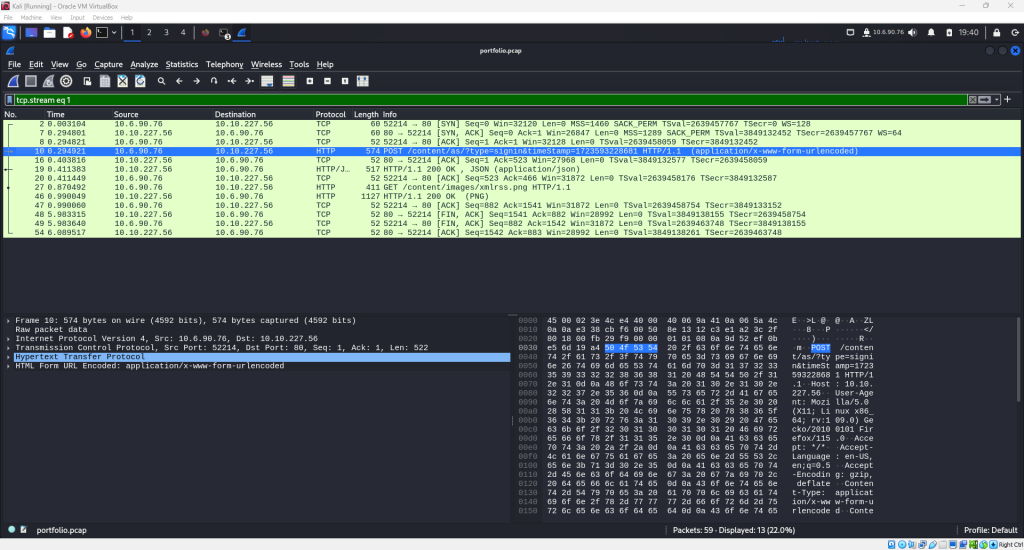
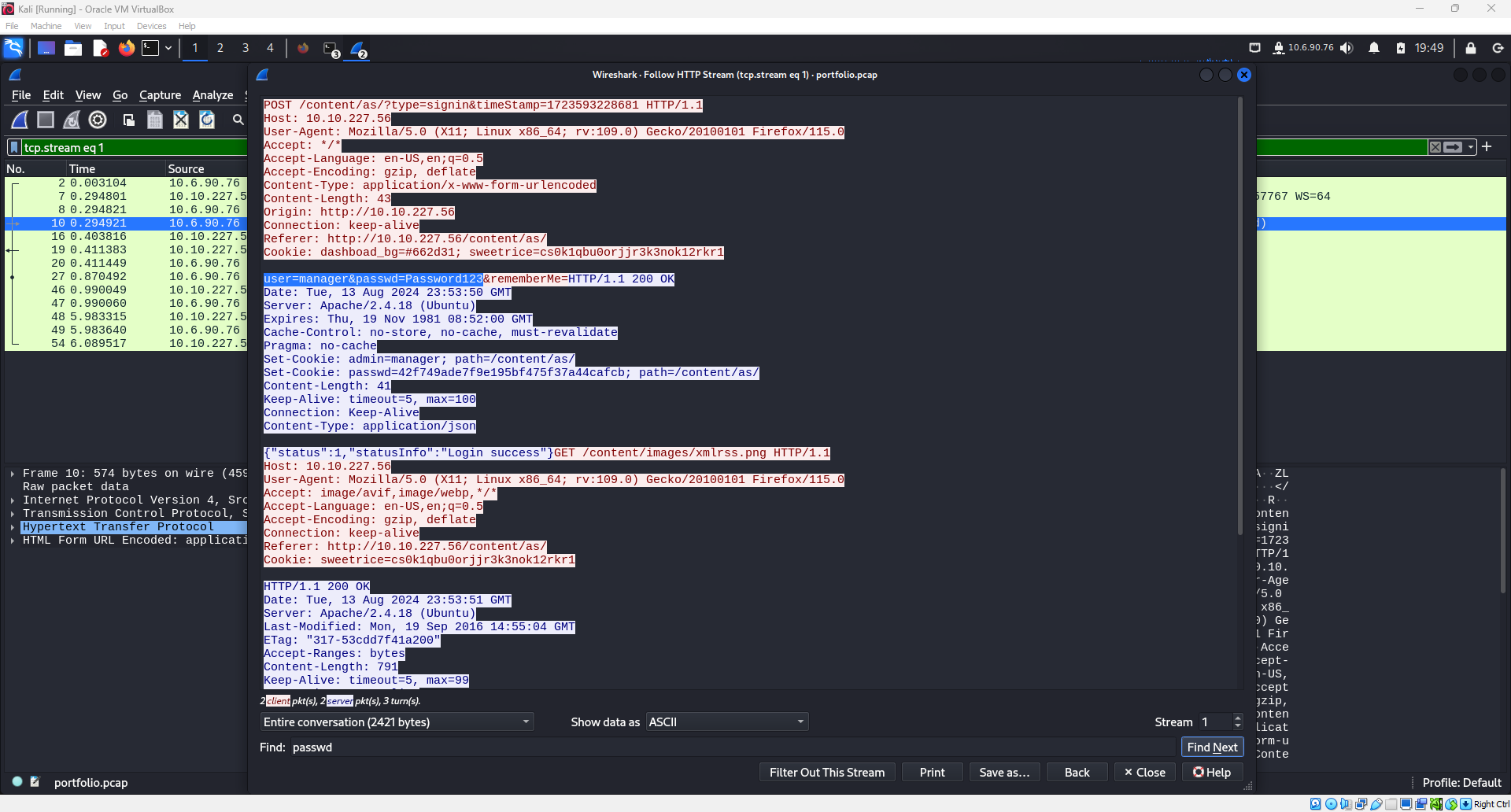
Upon examining the packets, it can be noticed quickly that near the top of the list, there is a packet with the HTTP protocol and some information that looks promising. Specifically, the “POST” action followed by the phrase “signin” is intriguing.
Right click on the packet and choose the option “Follow” from the drop down menu and then select “HTTP Stream” from the secondary drop down menu.
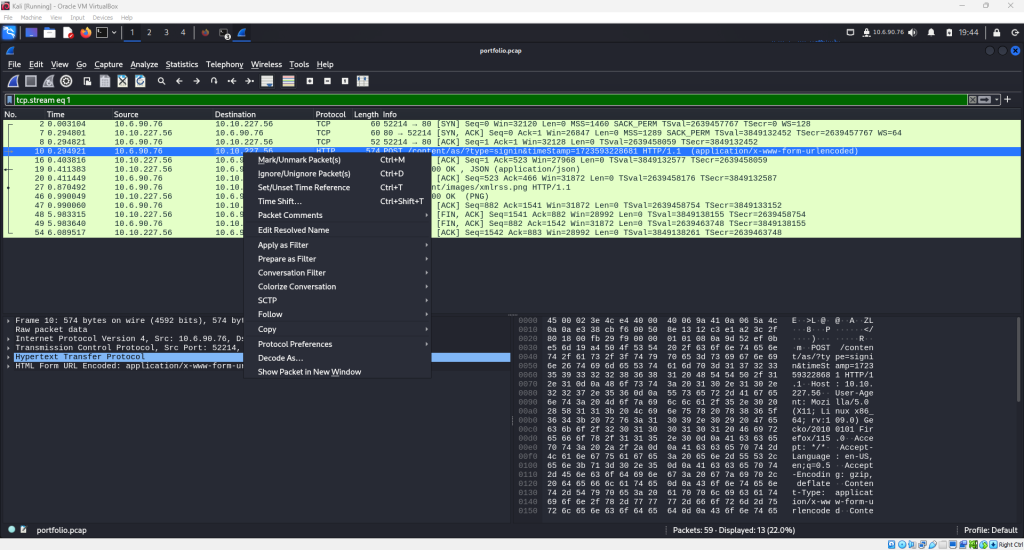
The HTTP Stream will appear and within it, the clear text username and password and be seen from a quick visual scan as highlighted in the screenshot below.
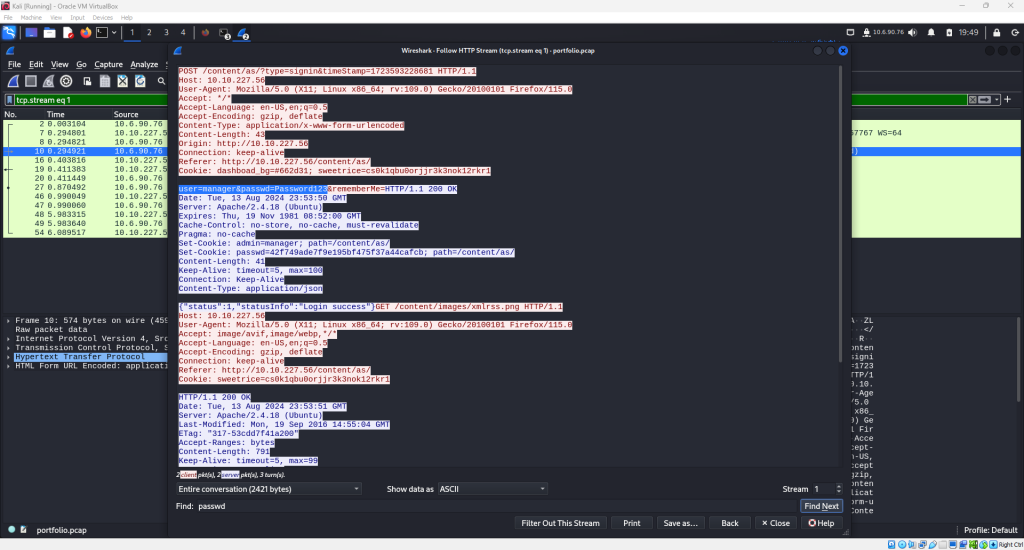
The important portion of the highlighted line reads “user=manager&passwd=Password123”.
The login credentials have been obtained.