This lab will demonstrate the process for creating a SIEM (Security Information and Event Manager) in Microsoft Azure. A functioning SIEM needs data to work with. That data will come from a newly provisioned Azure VM acting as a honeypot. Additionally, the process of creating a visualization of the data represented on a map will be detailed step by step.
- Step 1: Create a windows VM through the Azure portal
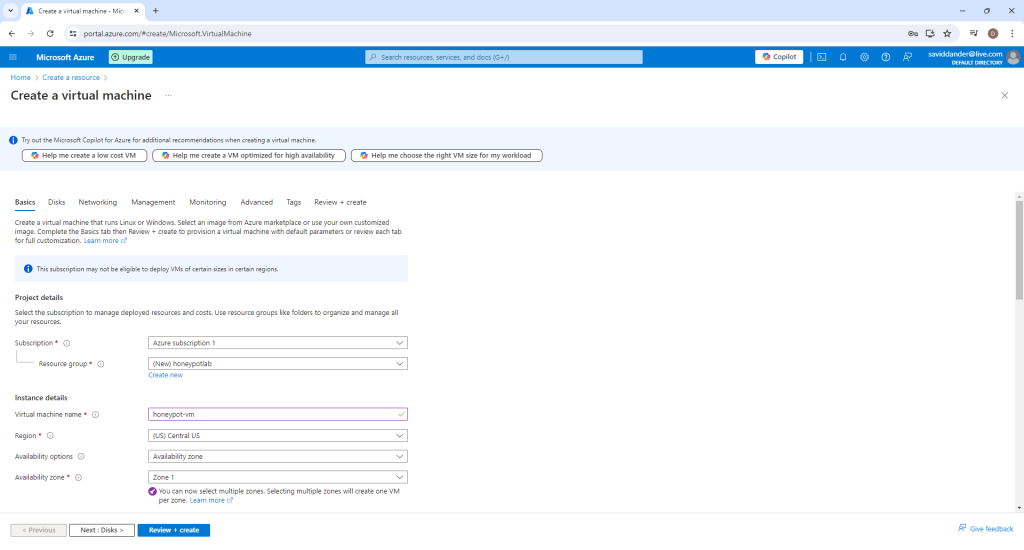
Choose a name and resource group for this VM (Something like honepot-vm is a good choice).
Most options can be left as default
On the “Networking” tab, select “Advanced” for the NIC Network Security Group. Then select “create new” next to “Configure network security group”. The page should look like the image below
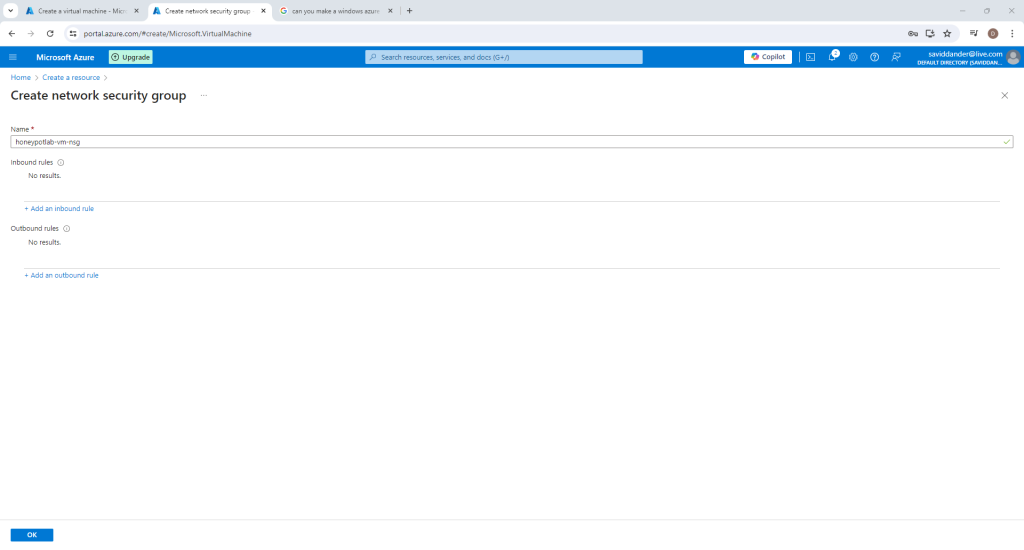
Delete any default inbound rules and select “+Add an inbound rule”. Create this rule with the specifications in the following image. (This will create a vulnerable machine to serve as the honeypot that will provide data for the SIEM)
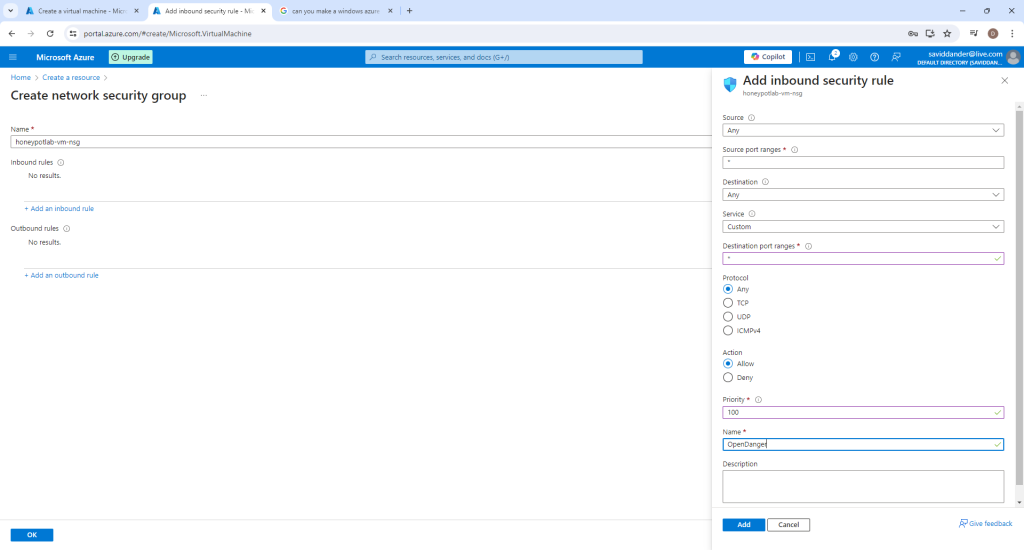
Add the new rule, select “Ok” and click “Create + review”. Once Azure’s validation is complete, create the VM.
- Step 2: Create a Log Analytics Workspace
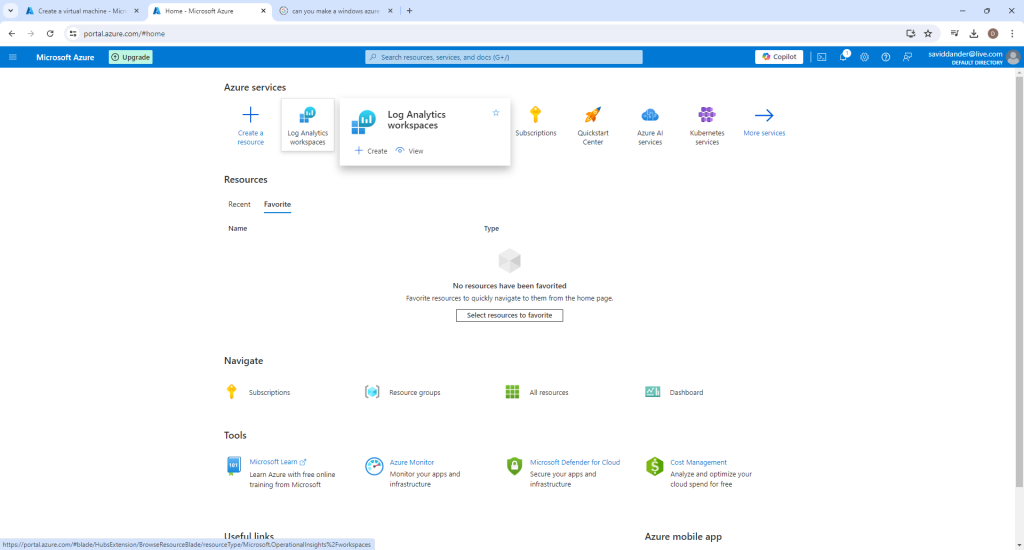
Create a new log analytics workspace and place it in the same resource group as the honeypot VM from the last step. Then select “Review + create” and then “Create” on the final page.
- Step 3: Enable Microsoft Defender for Cloud to gather logs from the log analytics workspace from the previous step
Go to Microsoft Defender for Cloud
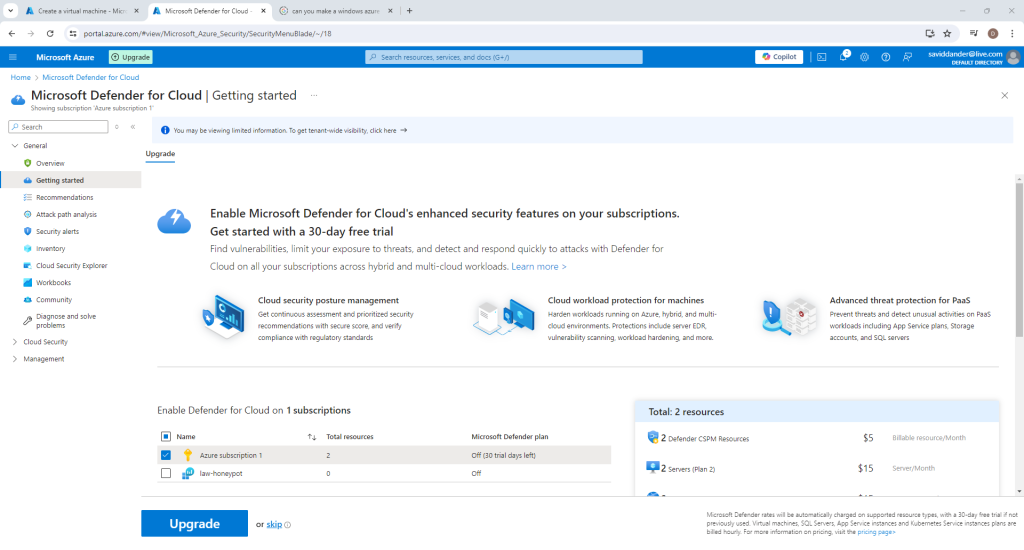
Select “Environment settings” from the panel on the left hand side and choose the log analytics workspace created in the last step.
Select “on” next to “Servers” to enable Defender for the log analytics workspace and then save.
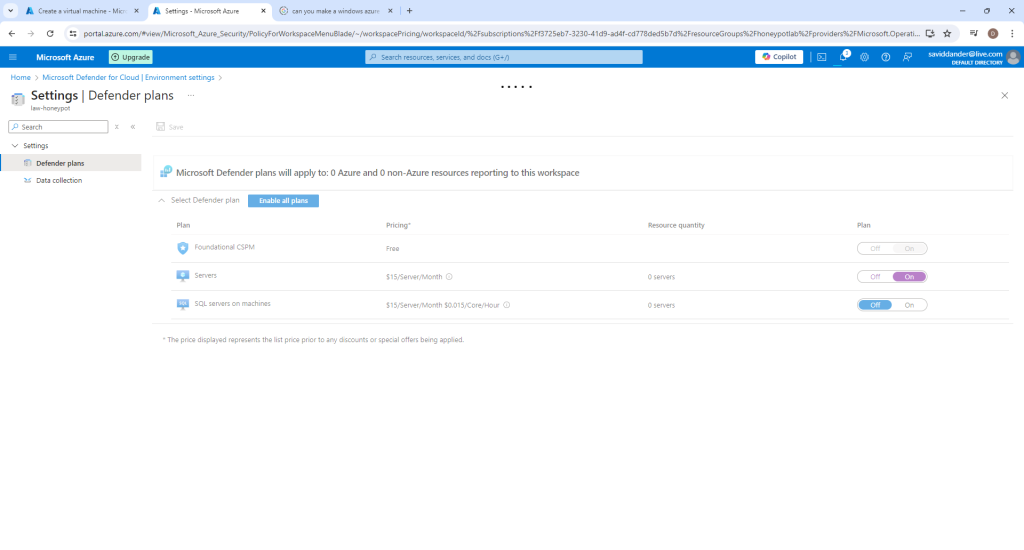
Switch to “Data Collection” on the left hand side panel and select “All Events” to be collected and click “Save”.
Return to the log analytics workspace page and select the newly created workspace from step 2.
Select “Virtual Machines” from the left hand panel and choose the VM created in Step 1. On the following page, click “Connect” at the top right. This process my take a few minutes.
- Step 4: Configure Sentinel
Navigate to Sentinel (this is easily done through the search bar at the top of the Azure portal
Select “Create Microsoft Sentinel” and choose the logs analytics workspace from previous steps and click “Add”. Again, this process may take a few moments
In the meantime, go back to the VM from step 1 and copy it’s public IP address
Open Remote Desktop Connection on a local machine and paste the IP address as shown below.
Select “Connect” and enter the admin credentials created in step 1 when prompted. It’s necessary to select “more choices” and “use a different account” to enter the admin credentials from the VM creation.
Once successfully logged in to the VM, deselect all the options on the following page shown below
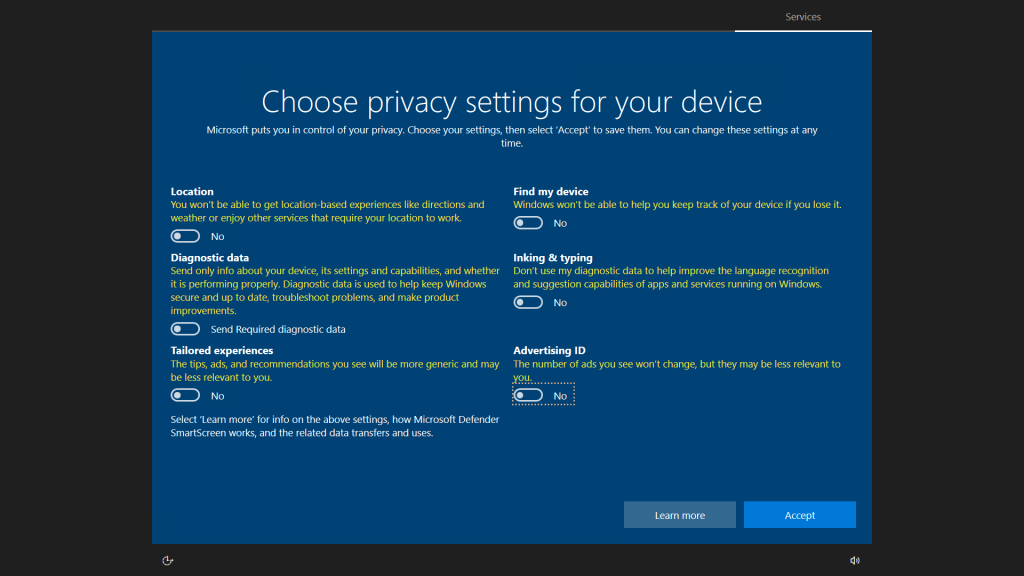
Upon arriving at the windows home screen, open the Edge internet browser and make the necessary selections to configure. (It is not necessary to sign in or sync personal data for this instance) . This will be useful later.
Navigate to Event viewer within the VM.
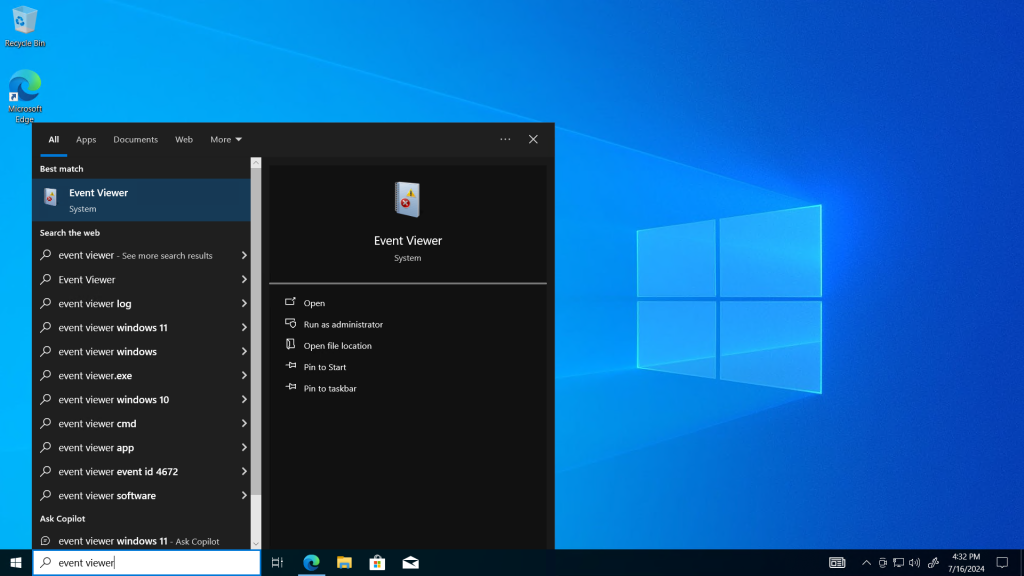
In event viewer, select Windows logs and then Security.
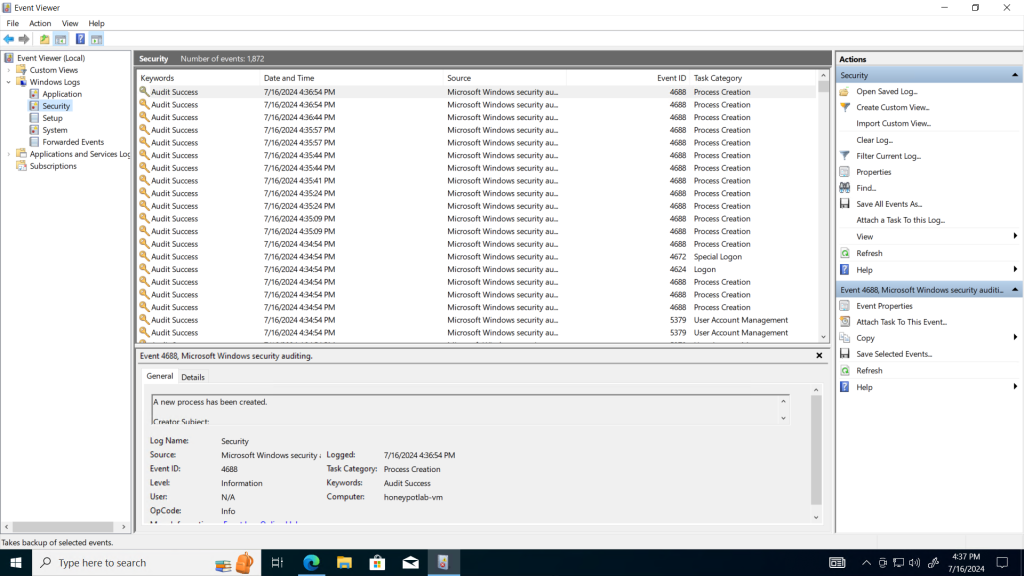
On this page in Event Viewer, it can be noted there was a failed login attempt (This was intentional). This attempt is an example of the type of data that will populate the instance of Sentinel(SIEM) created in a previous step.
As the unprotected VM is discovered by malicious actors across the internet, more attempts of this nature can be expected.
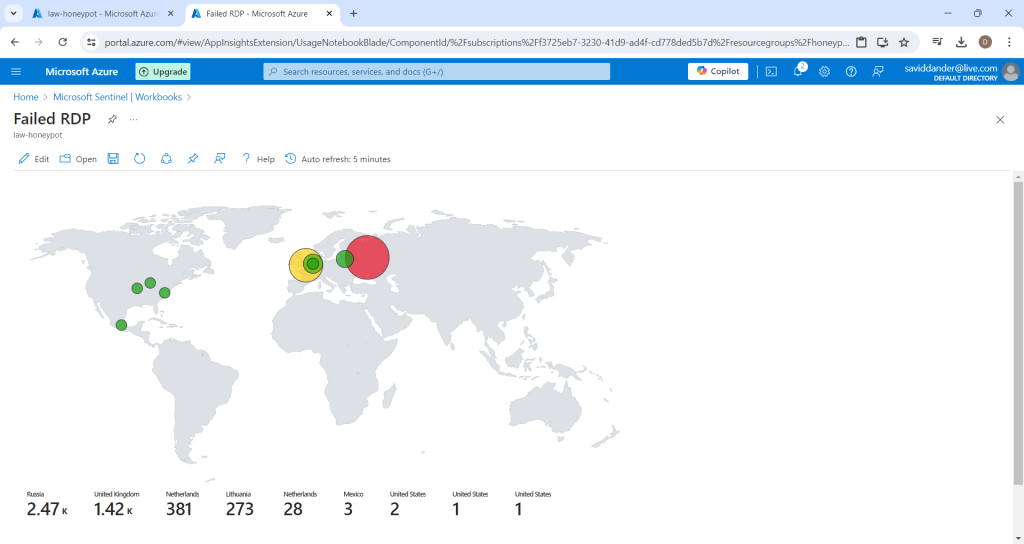
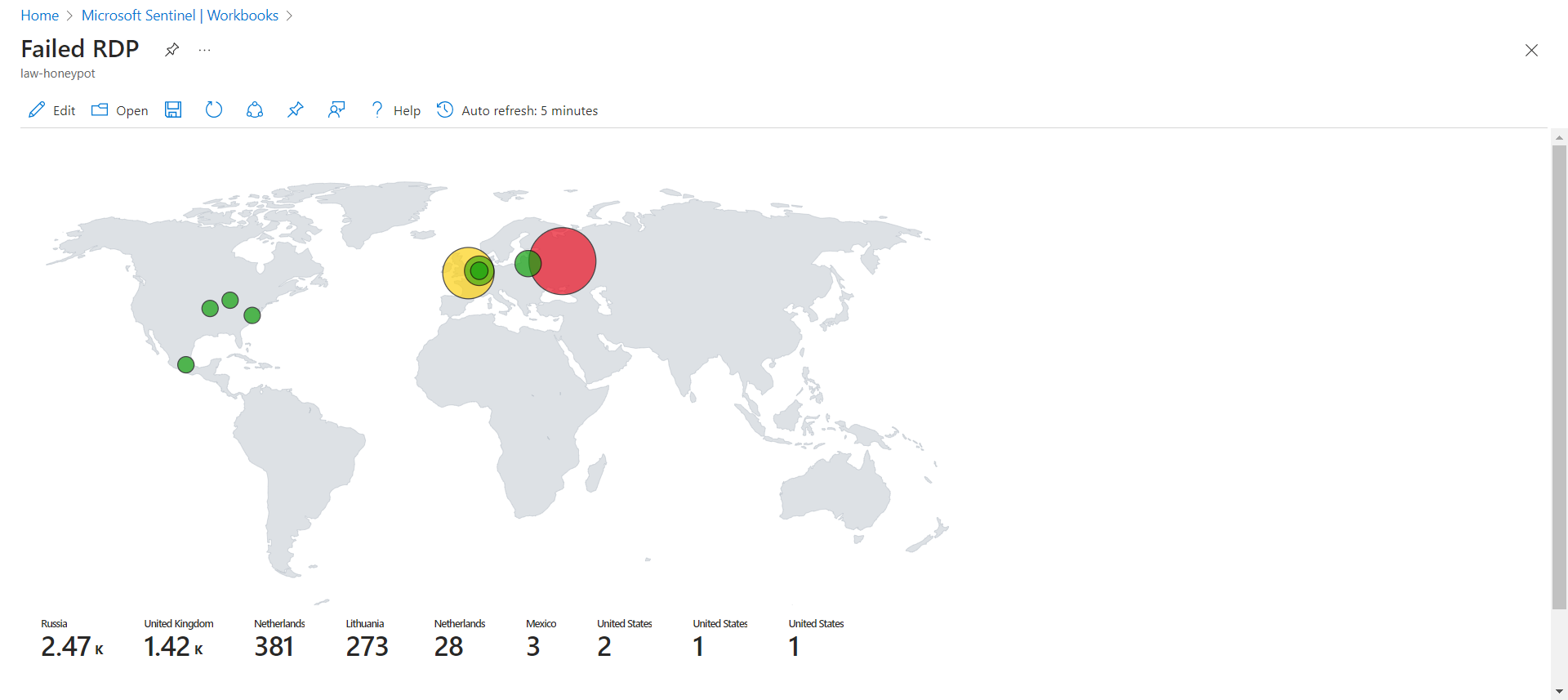
A SIEM allows for compiling these attempts and representing the data in an easy to ingest format. One valuable aspect of this data is it’s geographic metadata that, through the power of a SIEM, can display where the login attempts are originating based on IP address.
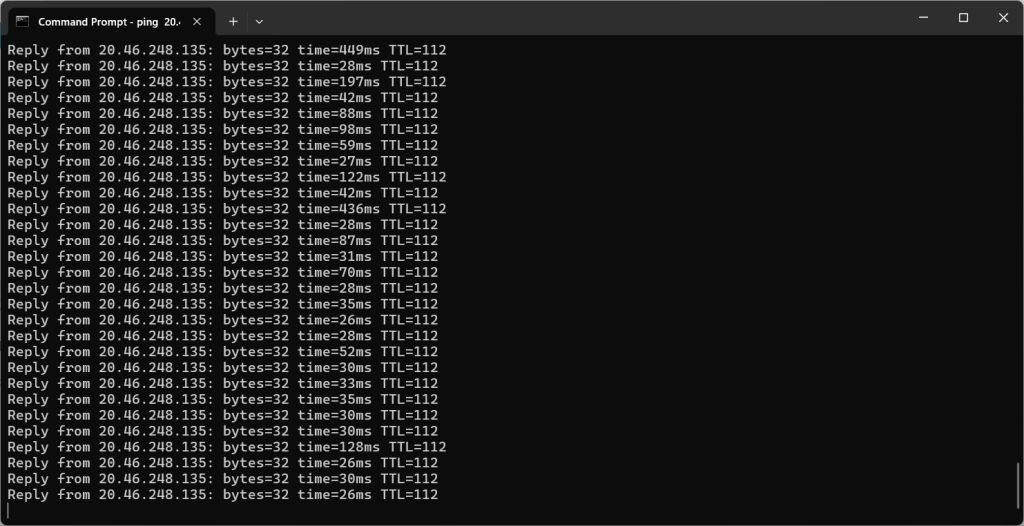
To ensure the honeypot VM is easily discoverable, copy it’s IP address and use the ping command in a terminal to reach it. (Shown below)
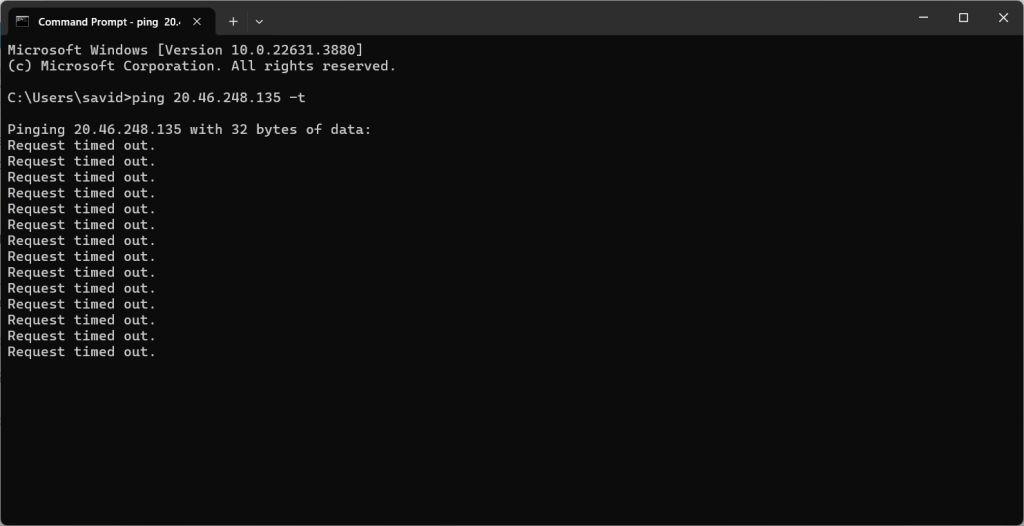
The above image shows the ping command is timing out. One solution to this issue is disabling the firewall on the VM (as seen in the next image)
Now, the ping command issued from the local machine is successful in reaching the VM as seen below
- Step 5: Use a Powershell script to automatically determine the geographic information of source IP’s attempting to access the honeypot VM
The necessary Powershell script can be copied at https://github.com/joshmadakor1/Sentinel-Lab/blob/main/Custom_Security_Log_Exporter.ps1
Next, run Powershell ISE on the honeypot VM, open a new script and past the copied script into the terminal. It should look like the following screenshot
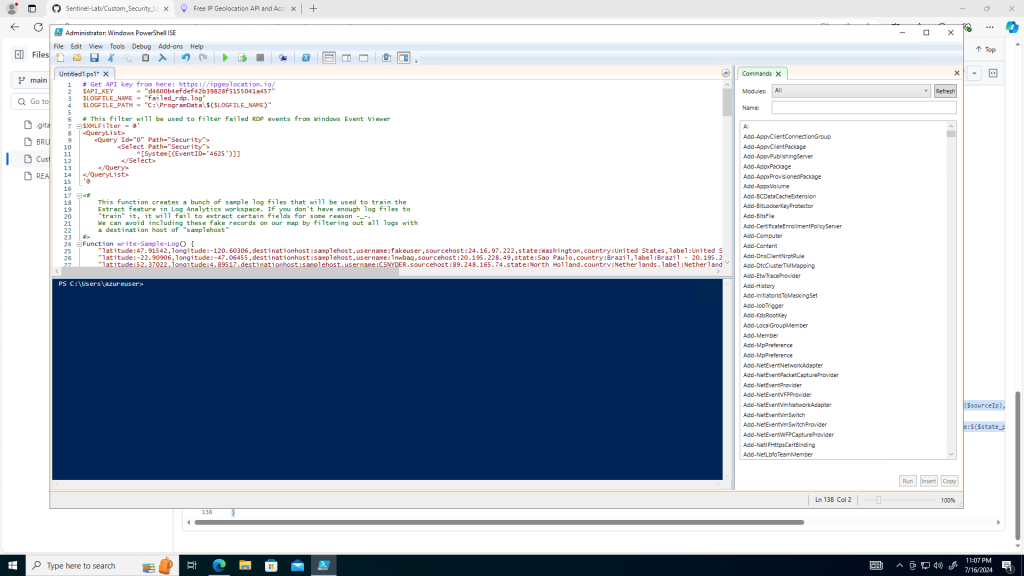
This script requires a personal API key from each user. This can be obtained by signing up at Sign up for ipgeolocation.io and copying the API key on the following page after successfully logging in.
Once the API key is copied, it must be added to the Powershell script in the location shown below
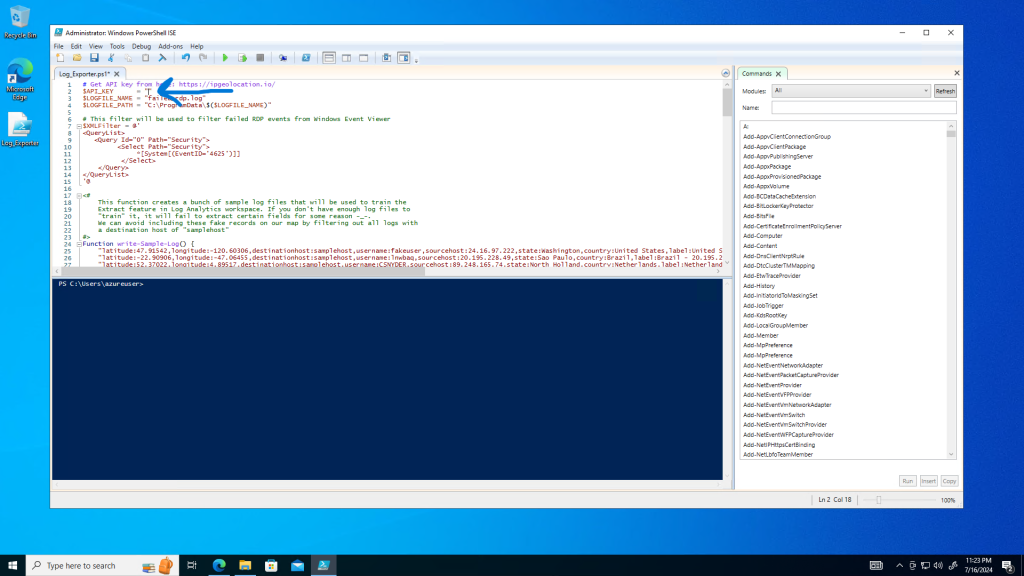
Save the script to update it with the new API key and then run it. The output should look similar to the screenshot below
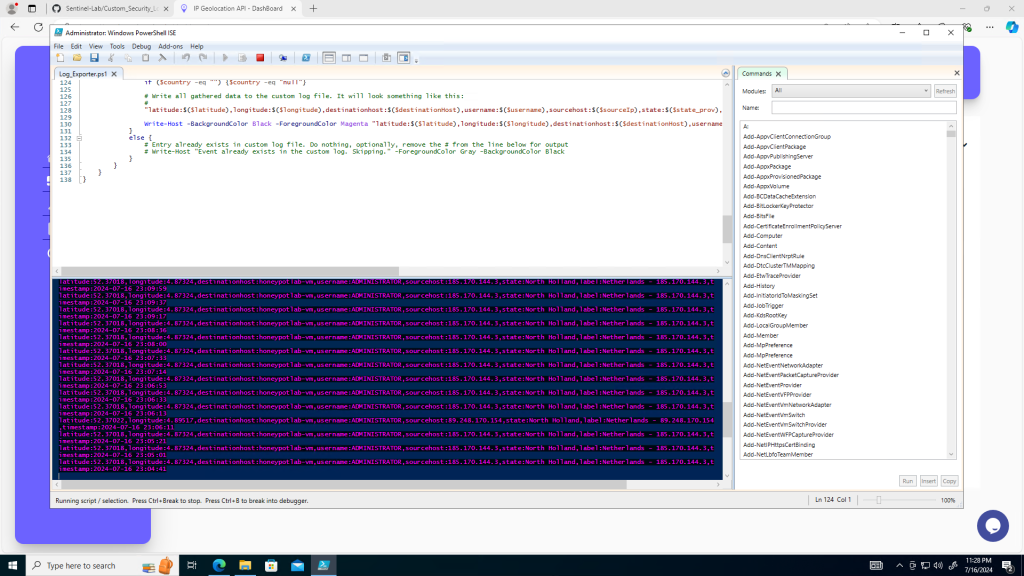
This output shows many failed login attempts from different source IP addresses across the globe.
- Step 6: Create custom log in the log analytics workspace through the Azure portal
Return to the log analytics workspace page in Azure, select the workspace created in the previous steps, click “Tables” on the left hand side panel and choose “Create”.
If prompted to select MMA-based or DCR-based for the custom log, choose MMA-based.
The first requirement for the custom log creation is a sample log file from the honeypot VM failed logins. Access this on the VM using the file path C:\ProgramData
The Powershell script from step 5 stores the failed login attempts in a file by the name “failed_rdp” (Shown below)
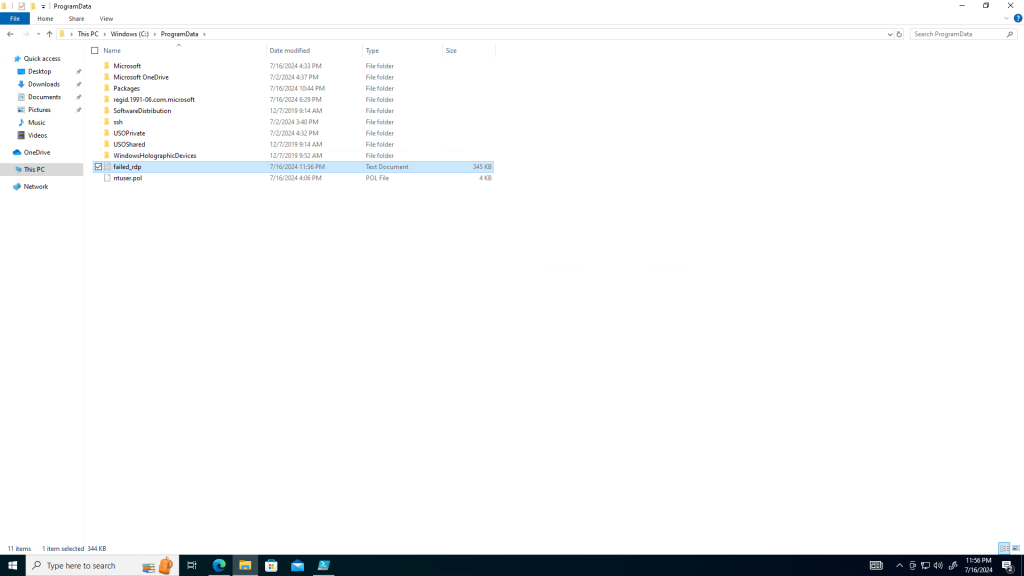
Because the file is on the VM and the Azure portal will browse the local machine, it is necessary to copy the log file from the VM, paste it into a document and save it on the local machine. From there, it can be uploaded to the Azure portal.
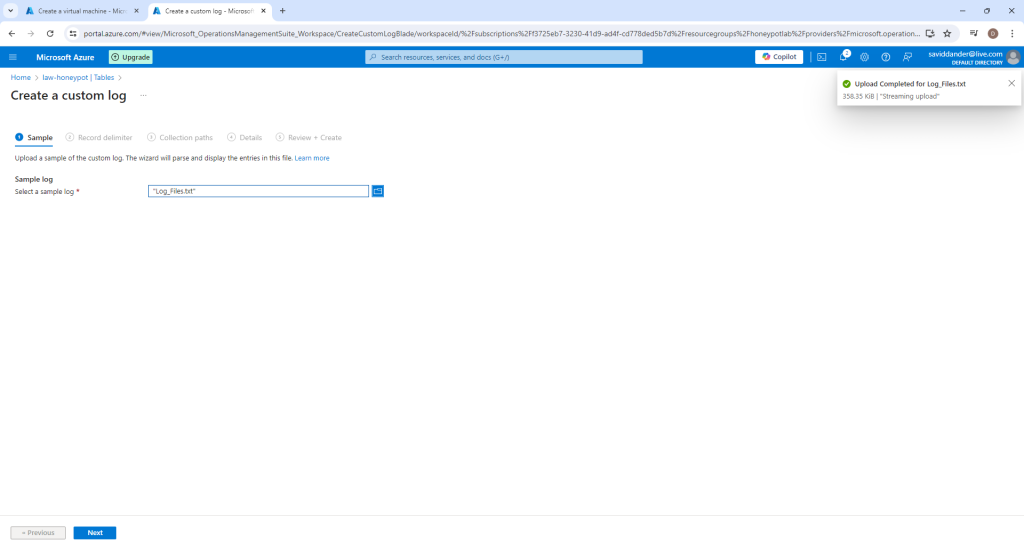
Once the log file is uploaded, select “Next” and enter the file path to the log file from the VM as in the screenshot below
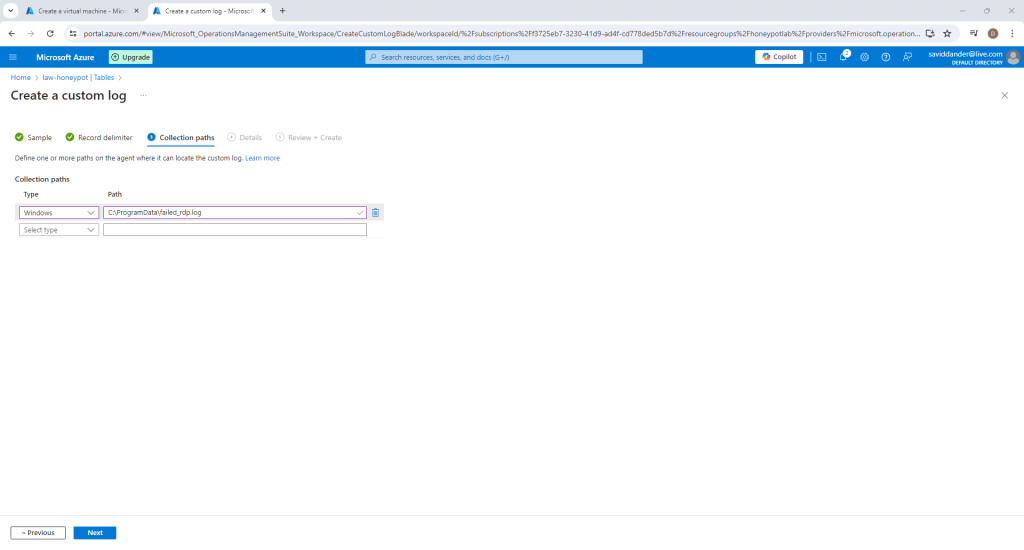
Click “Next” and give the custom log a fitting name and description and then select “Create”.
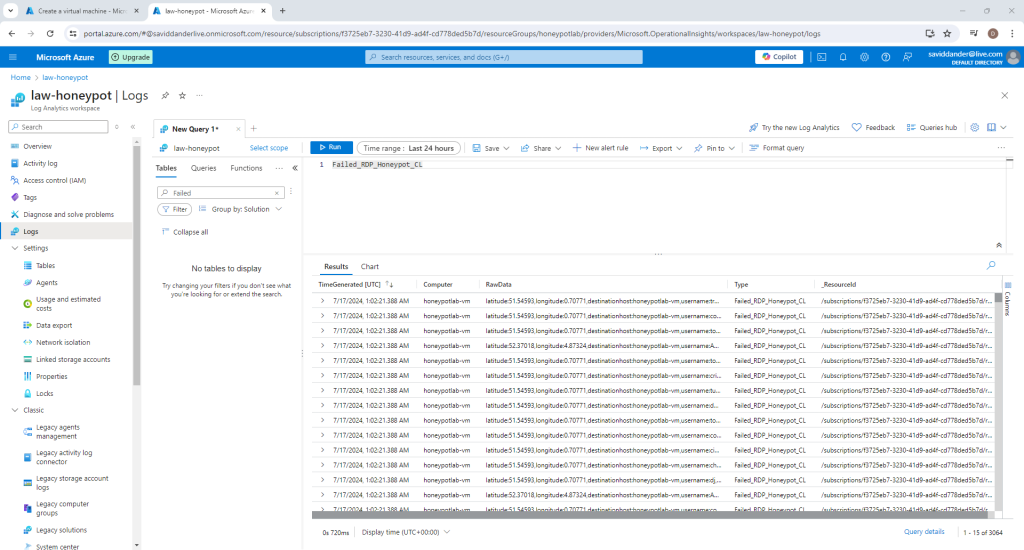
Once the custom log is created, navigate to log analytics workspace page, select “Logs” from the panel on the left hand side.
After some time, data will populate the custom log and can be seen by searching the name of the custom log as seen below
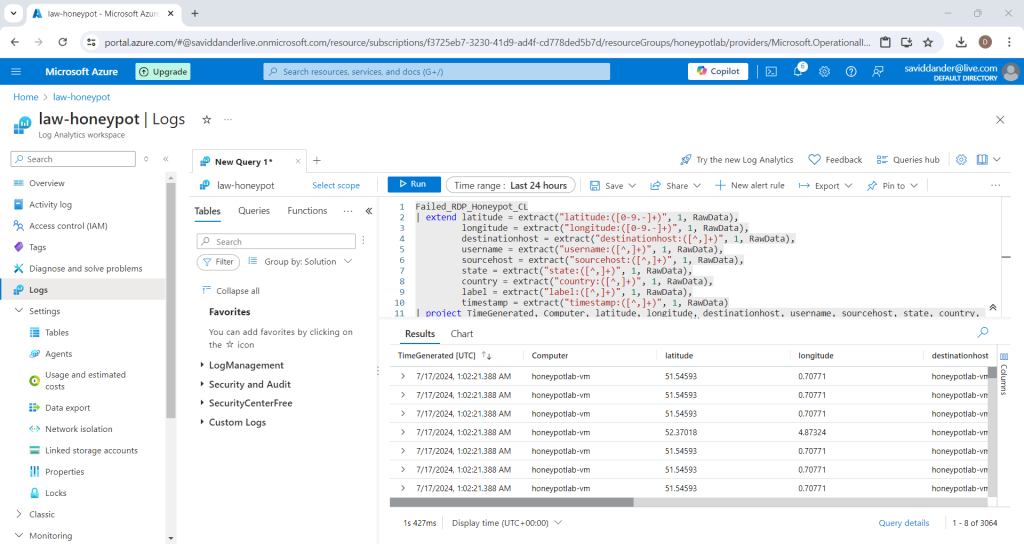
Run the following command underneath line one to separate the raw data into useful fields for the SIEM (Line one should be the name chosen for the custom log).
| extend latitude = extract("latitude:([0-9.-]+)", 1, RawData),
longitude = extract("longitude:([0-9.-]+)", 1, RawData),
destinationhost = extract("destinationhost:([^,]+)", 1, RawData),
username = extract("username:([^,]+)", 1, RawData),
sourcehost = extract("sourcehost:([^,]+)", 1, RawData),
state = extract("state:([^,]+)", 1, RawData),
country = extract("country:([^,]+)", 1, RawData),
label = extract("label:([^,]+)", 1, RawData),
timestamp = extract("timestamp:([^,]+)", 1, RawData)
| project TimeGenerated, Computer, latitude, longitude, destinationhost, username, sourcehost, state, country, label, timestamp )This will make the raw data appear as shown below
- Step 7: Setup map in Sentinel
Navigate to Sentinel (easily done through the azure portal search bar) and select the log analytics workspace created previously
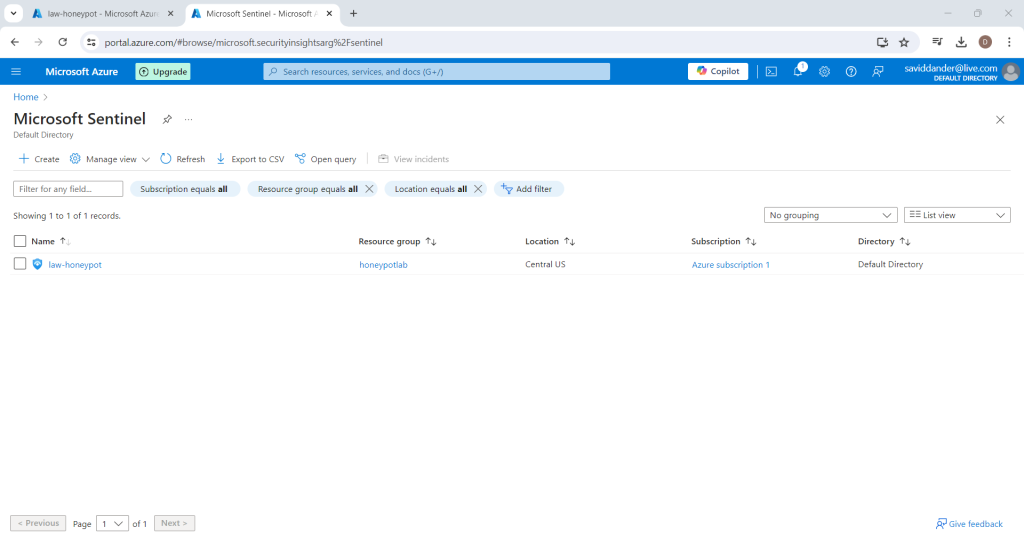
Select “Workbooks” on the panel to the left hand side of the following screen and then click the option to “Add workbook”
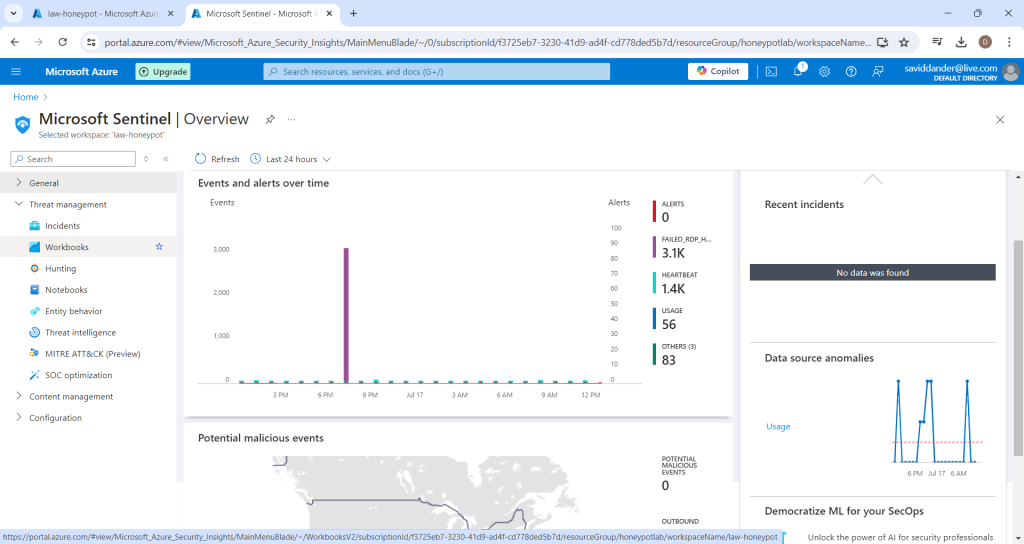
Choose “Edit” on the new workbook and remove any default graphs or charts. Then click “+ Add” and select “Query” from the dropdown list.
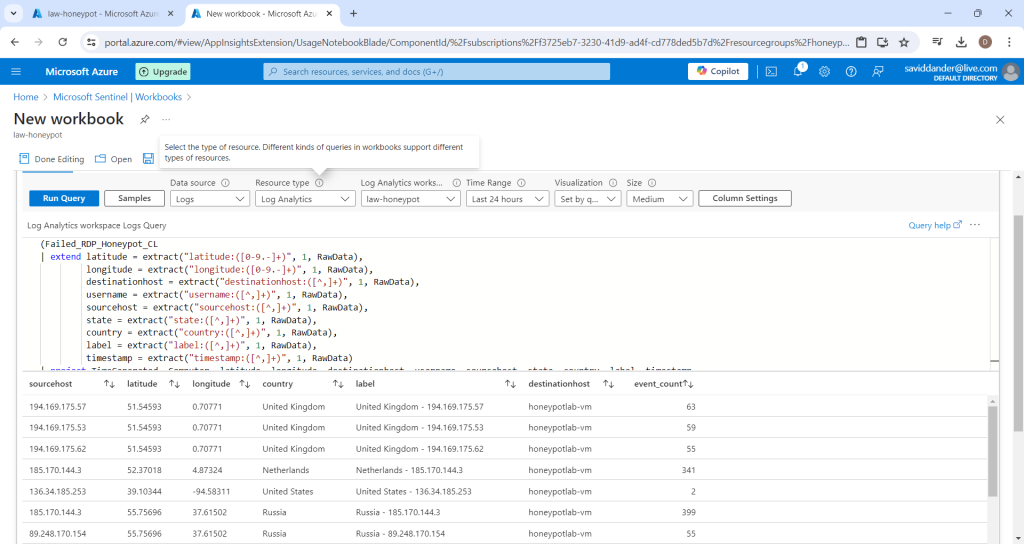
Now, paste the following command into the new Query box after line one (the first line should contain the chosen name for the custom log from step 6)
(Custom_log_name
| extend latitude = extract("latitude:([0-9.-]+)", 1, RawData),
longitude = extract("longitude:([0-9.-]+)", 1, RawData),
destinationhost = extract("destinationhost:([^,]+)", 1, RawData),
username = extract("username:([^,]+)", 1, RawData),
sourcehost = extract("sourcehost:([^,]+)", 1, RawData),
state = extract("state:([^,]+)", 1, RawData),
country = extract("country:([^,]+)", 1, RawData),
label = extract("label:([^,]+)", 1, RawData),
timestamp = extract("timestamp:([^,]+)", 1, RawData)
| project TimeGenerated, Computer, latitude, longitude, destinationhost, username, sourcehost, state, country, label, timestamp
| summarize event_count=count() by sourcehost, latitude, longitude, country, label, destinationhost
| where destinationhost != "samplehost"
| where sourcehost != "")Run the query and an output like the one below should be displayed
Select the drop down menu for “Visualization” and choose “Map”. The layout settings on the right hand side panel should default to latitude/longitude for the data’s location information.(Shown below)
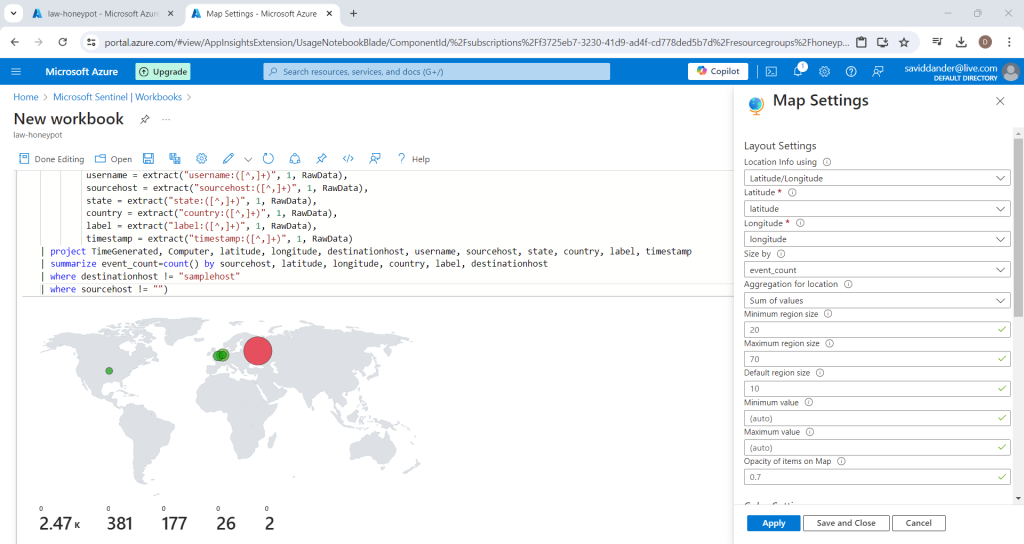
A variety a options can be manipulated to tailor the appearance of the data on the map.
Next, select the save icon and choose a name for the map. Additionally, the “Auto refresh” option can be modified to represent data as it is received. Choose an increment for the frequency at which the map will refresh.
The Powershell script implemented earlier must be running to introduce new log data and be reflected on the map.
After only a short time, the map will begin to display additional geographic data similar to the the image below