Using Kali Linux, this exercise will walkthrough the process of creating a custom rule in Suricata to alert on an attempted telnet connection from a remote host.
First, open a command terminal in Linux and navigate to the directory containing the rules for Suricata. (seen below in the upper left terminal)
Having multiple terminals open will be helpful in this exercise.
Once inside the Suricata rules’ directory, use the following command to create a new rule:
nano <rulename>.rules
Add to sudo to the beginning of the command if performing as regular user.
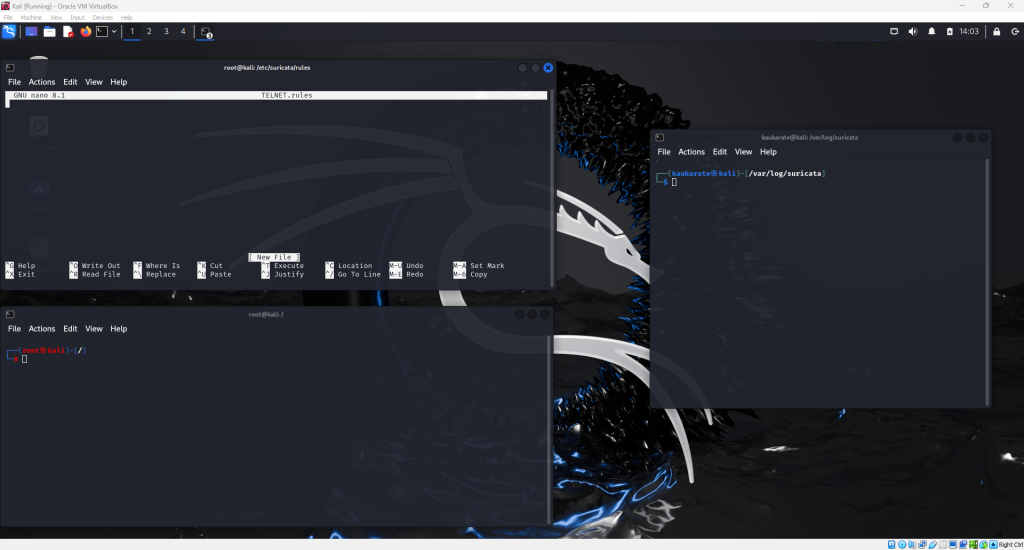
This opens a window as seen above where a new rule can be written.
For this example, a rule blocking telnet connections will be created.
Suricata rules begin with an action, contain a header and end with options. The image below displays the format for this given rule.
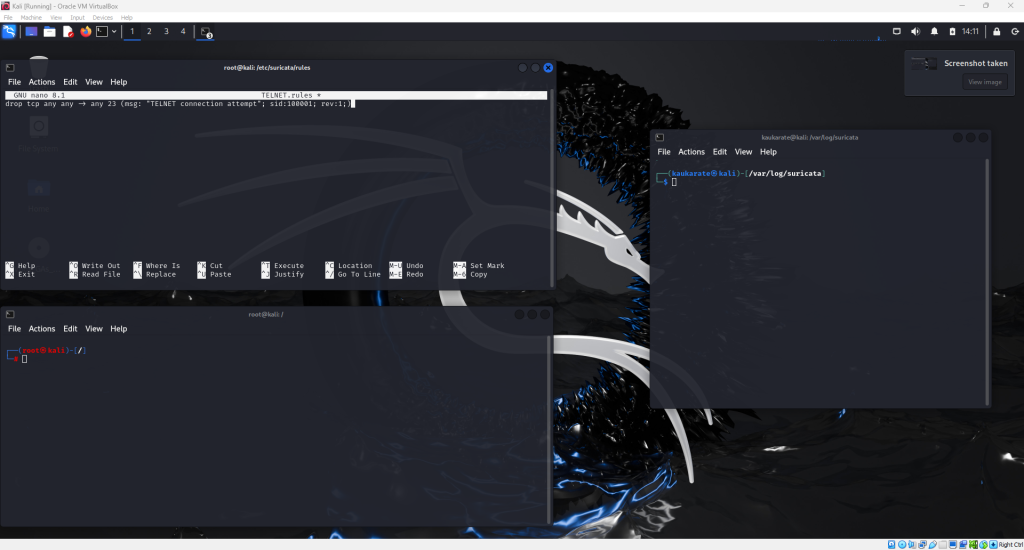
alert tcp any any -> any 23 (msg: “TELNET connection attempt”; sid:100001; rev:1;)
This rule will alert on any tcp traffic coming into port 23 on the target machine and display the message “Telnet connection attempt” in the logs.
Now, save the rule and return to the command terminal and enter the following to run Suricata focused exclusively on this new rule.
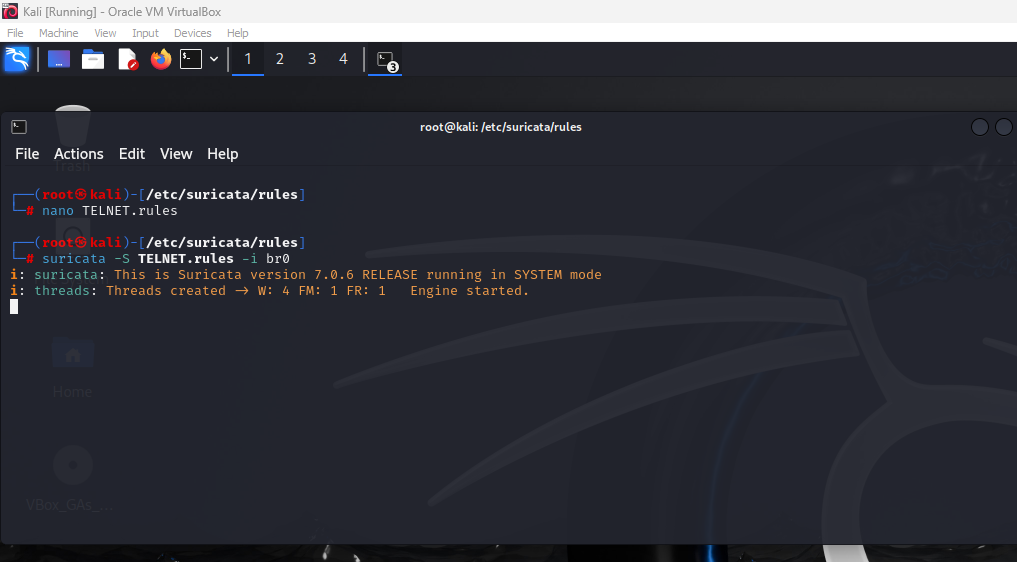
(It is necessary to add the appropriate rule name and interface to the above command)
In a separate terminal, navigate to the directory containing the logs for Suricata.
Now, to demonstrate the Suricata telnet rule is working, attempt to telnet to the host machine from another remote host.
The example below shows an attempted telnet connection from a windows host.
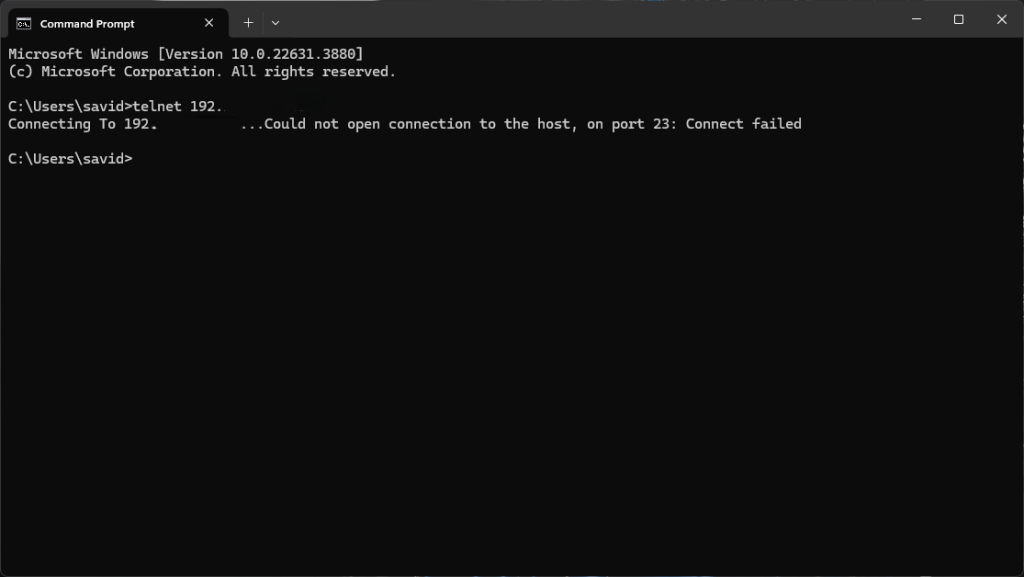
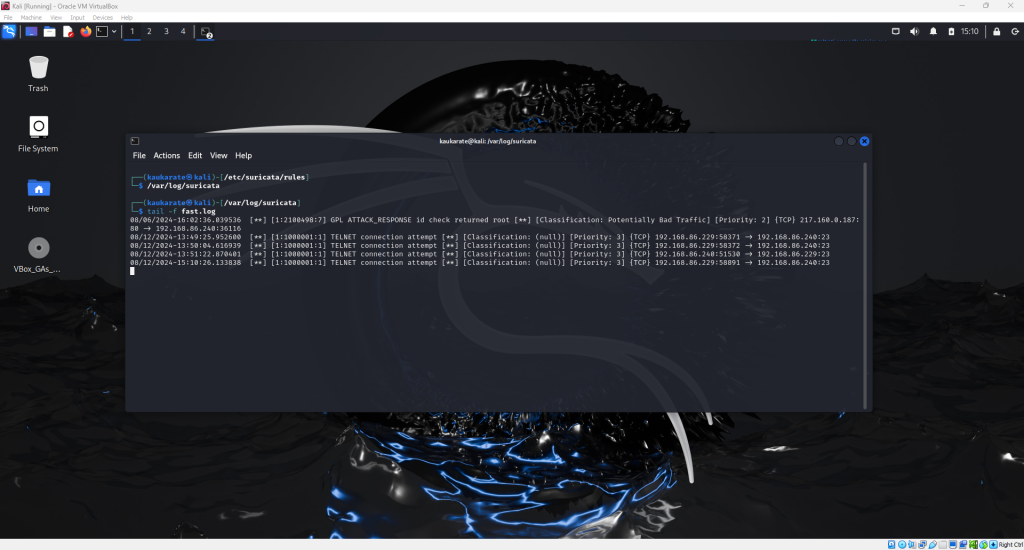
The connection was unsuccessful, but the logs from Suricata will indicate the attempt was made.
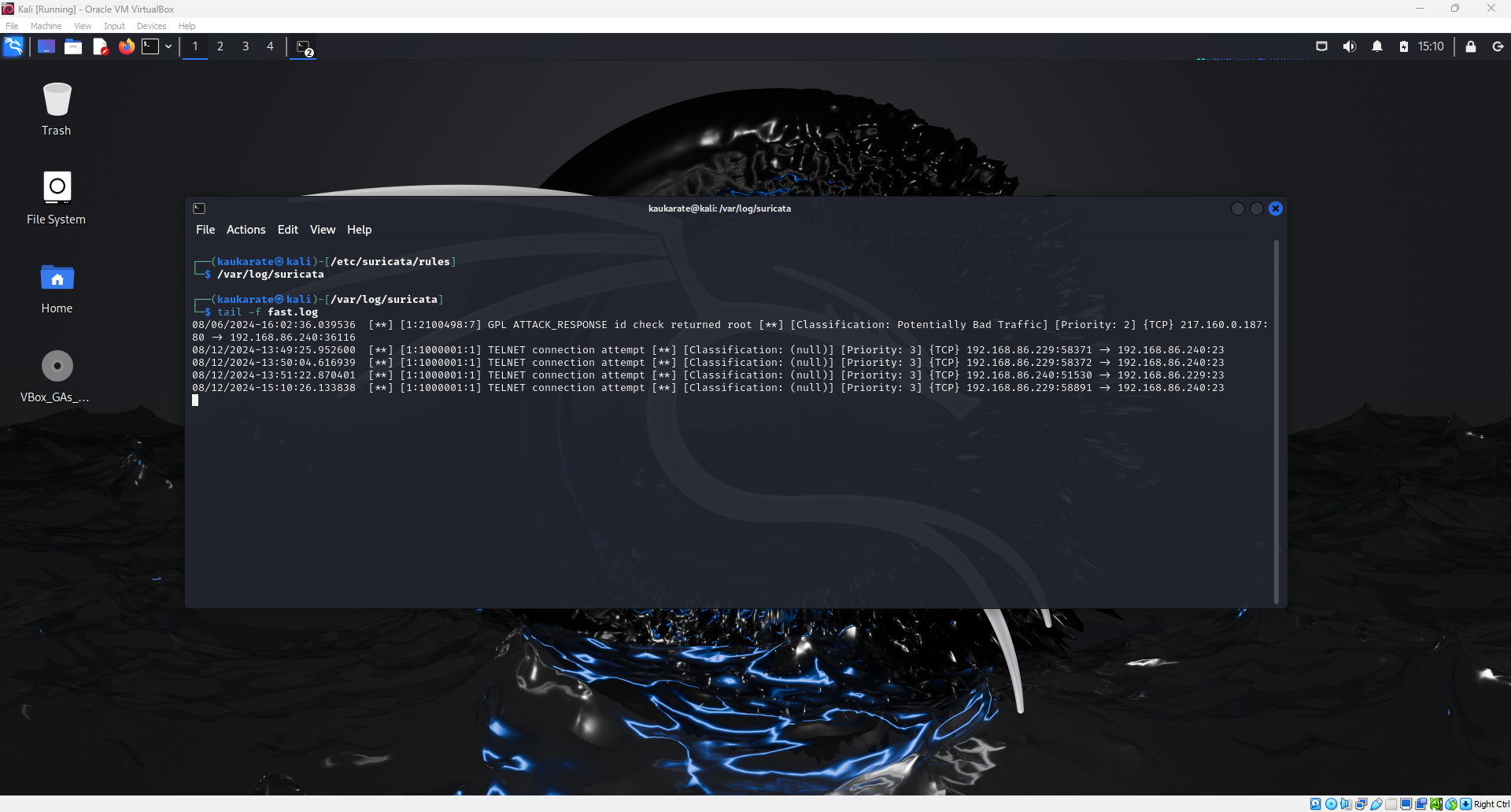
Return to the Linux terminal in the Suricata logs directory and enter the command seen below to display the most recent logs. The telnet connection attempt from the windows terminal will be reflected as seen below